We previously wrote about why you need a password manager, but actually getting your team or employees to use one is a bit more challenging. Here’s a concise guide to make that a bit easier. This guide assumes an administrator has created employee accounts.
In this guide:
- Quick Start
- What Goes in Your Password Manager
- Why Does This Even Matter
- Setting Up Multi-Factor Authentication (MFA)
- Browser Extension vs. Mobile App
- Why Not Just Use Chrome’s Built-In Password Storage?
- Sharing Passwords Securely
- Using Your Password Manager Day-to-Day
- On Security Questions
- Common Concerns
Quick Start
New to password managers? Here’s how to start making your logins faster.
1. Install the software
Your software will vary and could be Bitwarden, 1Password, Keeper, or another mainstream trusted application.
- Install the browser extension for your standard Chrome/Edge/Firefox
- Install the mobile app, if appropriate
2. Create your master password
This is the one password you’ll need to remember. Make it a unique phrase. Length and uniqueness are most important, but you may add numbers and symbols. Aim for at least 20 characters.
Don’t worry, you won’t have to type this constantly. At most once per day, but likely only when your computer or browser restarts.
For example:
3Trillion-Hungrily-Subdued-Peanuts
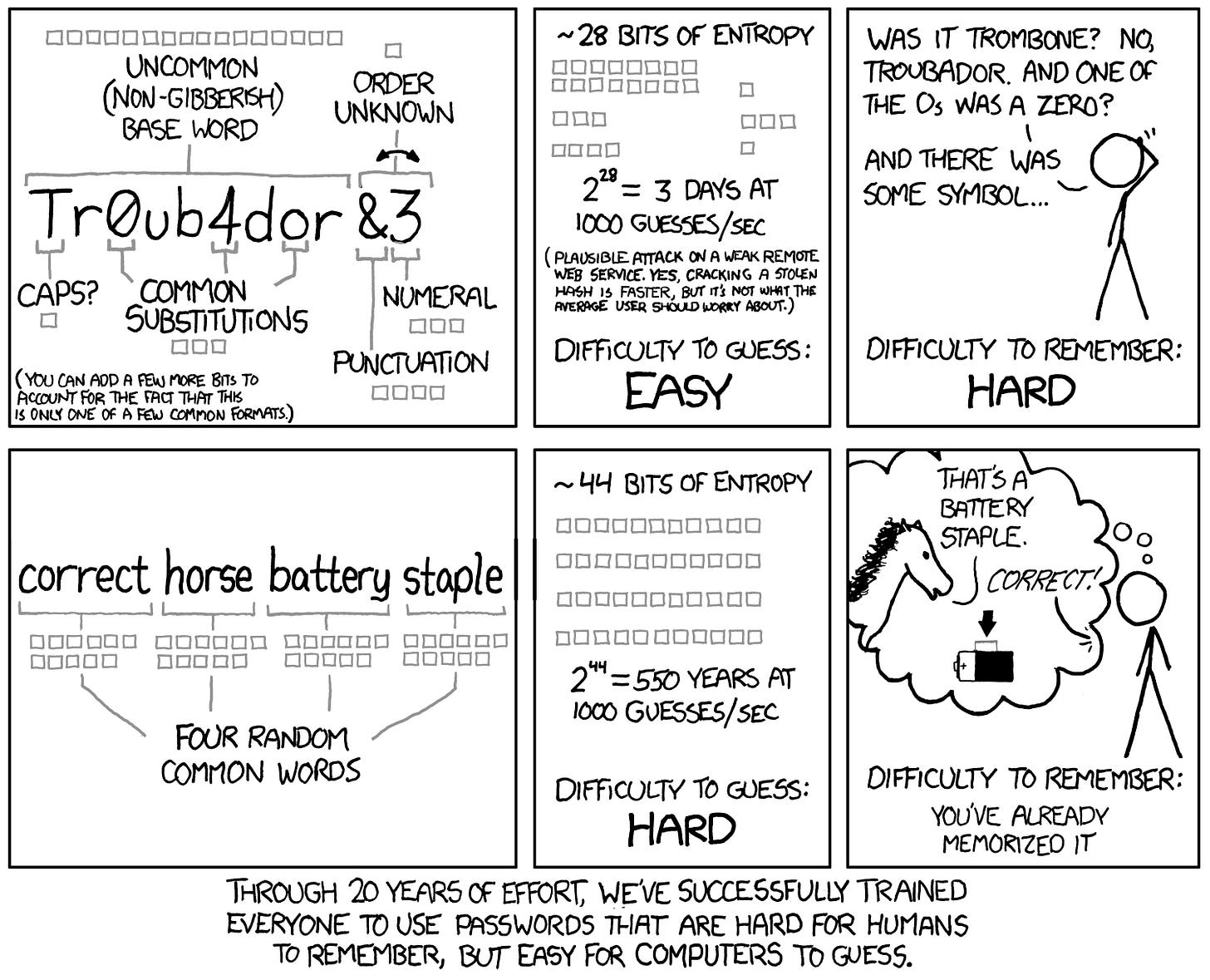
Create your own unique phrase. Think of a random combination of words that means something only to you, then add numbers and symbols.
Print it out and store it in a safe place. You’ll understand why this matters in a moment.
Then, enable multi-factor authentication on your account - preferably two passkeys, on both a work laptop and a work phone.
3. Disable Chrome’s password saving
- Open Chrome Settings → Autofill → Passwords
- Turn off “Offer to save passwords”
- Turn off “Auto Sign-in”
More on why you want to do this below.
4. Migrate any passwords from files
If you have passwords in text files, spreadsheets, or notes:
- Copy each password and add it to your password manager
- Verify it saved correctly
- Delete the original file and empty your trash
5. Start adding accounts
As you log into work systems over the next few days, save each password to the manager when prompted.
Non-Negotiables
- Store all work passwords in your password manager, without exception
- Use the built-in password generator for new accounts
- Never share passwords through email, chat, or text (use the password manager’s Share feature instead)
Make Your Life Easier
- Enable auto-fill to speed up logins
- Check the security audit feature which will tell you if you're using weak or reused passwords. Don't ignore this - it's literally how attackers gain access to accounts every day.
- If necessary, install the mobile app for access away from your desk
What Goes in Your Password Manager
Always Add
- Website logins for all work apps (Google Workspace, Microsoft 365, etc)
- Banking and financial information
- Security question answers
- SSH keys or API tokens for developers
Don’t Add
- Personal account passwords - these should go in your Personal Password Manager since you want to take those with you if you leave your job
Why Does This Even Matter
Password managers seem unnecessary until you understand the alternatives. Weak passwords, reused passwords, and passwords saved in files create security vulnerabilities that put the entire company at risk.
The core principle is making it harder for attackers. There are two primary security benefits beyond not having to remember passwords.

1. Reused Passwords with Website Breaches
When one website gets breached, your unique password on that site means that no other accounts you have on other systems are affected. Without a password manager, maintaining unique passwords for dozens of work systems is unrealistic, so people reuse passwords. That’s how one breach becomes ten breaches.
Long ago, a LinkedIn user reused the same password across his accounts. When LinkedIn was breached, attackers tried that password everywhere and gained access to his email, the company’s email, the company’s CRM, and the analytics dashboard. Those breaches went undetected for weeks. Using unique passwords for everything, which is only realistic with a password manager, would have limited the damage to LinkedIn.

2. The Manager Can See Phishing Pages
When you click on a link that leads to a perfect replica of a login page, your password manager knows it’s not the legitimate site and will not auto-fill or present the password for entry. This should give you pause to check the site's URL before entering your credentials. If you don’t recognize it, retrace your steps—how did you get to this page?
When you get that (im)perfectly timed email about a document shared with you, that redirects you to log in to Microsoft for security purposes, and you enter the credentials (and your MFA text code), and then your account is used to send thousands of spam emails and your SharePoint data is stolen, everyone has a bad day. Not knowing your Microsoft login credentials and relying on your password manager to determine whether the URL is legitimate would have stopped all of that before it was compromised.
Setting Up Multi-Factor Authentication (MFA)
Adding MFA - also called Two Factor Authentication (2FA) and even Two-Step Verification (2SV) - to your password manager provides an extra security layer. It’s kind of like needing two keys to open a safe - even if someone steals one key (your master password), they’d still need the second key (your phone or authenticator app) to get inside.
The setup process is a bit of a pain:
- In your password manager settings, enable two-factor authentication
- Choose “Passkey” (recommended for most people unless your organization has unique requirements), Yubikey, “Authenticator app”, or phone number
- Add a second MFA method in case one is lost or unusable
- Save the backup codes in a secure physical location - mandatory
- Test it by logging out and back in
Pro Tip: Not all MFA is created equal. “Phishing-resistant” authenticators like passkeys and most YubiKeys check the website name before sharing the secret. Authenticator Apps and SMS don’t, and can be intercepted by attackers.
Browser Extension vs. Mobile App
If you use your mobile device for work (not simply email), install both the extension and the mobile app. Otherwise, just the browser extension.
Browser Extension (Daily Use)
This is your primary tool. It autofills passwords directly into login forms and saves new credentials instantly. Most people use this many times per day.
Mobile App
Access work passwords when you’re away from your desk. Essential for checking systems while traveling or working remotely.
Why Not Just Use Chrome’s Built-In Password Storage?
Chrome’s password manager doesn’t support centralized IT management, doesn't provide an audit trail, and doesn't support secure team sharing, whereas password managers do.
The key difference is that if your laptop is stolen or malware runs on your computer, a hacker or someone who gains access to your account can access your Chrome passwords.
Your password manager requires a completely separate master password, different than your computer login.
Sharing Passwords Securely
Sharing passwords should be the exception, but it can be necessary.
For temporary access, use your password manager’s “One-Time Share” feature. The recipient gets access once, then it expires automatically.
For permanent team access, add passwords to shared folders (like “Marketing Team” or “Dev Tools”). Everyone with folder access automatically gets the credentials. When someone leaves the team, remove them from the folder—they lose access immediately.
Never share passwords via Email, Slack, Teams, or other chat apps, or recorded video calls. Passwords exposed in chat and email are left there for hackers to find and abuse later.
Using Your Password Manager Day-to-Day
Adding new accounts:
- Click “Generate Password” when creating the account
- Set length to 20 characters (or the site’s maximum)
- Include symbols unless the site doesn’t allow them
- Save immediately after creating the account
Updating existing passwords
Start with critical accounts: email, financial systems, and administrative tools. Then gradually update everything else. The security audit feature (see below) will identify which passwords need updating most urgently.
Auto-fill
When you visit a login page, your password manager shows matching accounts. Click to auto-fill. This saves most people 5-10 minutes per day and eliminates typos.
On Security Questions
Security questions are a weak point in many systems. Answers like your mother’s maiden name or the city you were born in can be discovered through social media or public records.
A better approach - Generate a password using the password manager and use that as an answer. Store it in your password manager.
For example:
- Question: “Mother’s maiden name?”
- What you enter in the website:
q7RxM2pK9wL
- What you enter in the website:
- What you store in your password manager
- Question: “Mother’s maiden name?” / Answer:
q7RxM2pK9wL
- Question: “Mother’s maiden name?” / Answer:
Common Concerns
“What if I forget my master password?”
This is the most serious risk. Your password manager uses something called “zero-knowledge encryption,” which means it’s like a safe where even the safe manufacturer doesn’t know the combination. If you forget your master password, you’re locked out. Permanently. Most password managers can’t reset it because they literally don’t have a copy. IT should be able to help with organization accounts, but you’re out of luck with personal accounts. That's mostly not a lie - many products provide you a recovery key or emergency kit for safekeeping.
How to prevent that?
- Print your master password and store it in a safe place at home
- Print your 2FA backup codes and store them with your master password
- Consider sharing access with a trusted person using your password manager’s emergency contact feature
- Add a backup MFA method
“What if the password manager company gets hacked?”
This has happened (LastPass was breached in 2022), but the encryption design means hackers can’t read your passwords without your master password. Even if thieves break into the bank vault, your individual safe deposit box still requires your key. The company’s servers are the vault; your master password is the key to your box.
This is why your master password must be strong: unique, and very long. Weak master passwords put you at risk even if the encryption is strong. Many LastPass users lost cryptocurrency after hackers guessed their weak master passwords and subsequently their wallet information.
“What if I need to access passwords but don’t have my device?”
Install the mobile app now, before you need it. You can access your vault from any device by logging in to the web interface, but you’ll need to remember your master password and have your 2FA method ready.