Update: The CMMC Final Rule has been released. Organizations seeking Level 1 CMMC status will need to comply with 15 requirements outlined in FAR 52.204-21.
You, too, can follow along with this 50-page PDF CMMC Self-Assessment Guide.
The FAR 52.204-21 “Basic Safeguarding of Covered Contractor Information Systems” outlines what you must do if you have non-public government contract information available at your business.
Here’s how you can quickly move towards becoming more secure and compliant.
Scoping
Every business should consider these items as a general business resilience practice, but CMMC is specifically concerned with protecting Federal Contract Information (FCI) and Controlled Unclassified Information (CUI)—the non-public data.
Before you can start, you’ll need to start writing down where this information is coming from, where it’s going, where it’s being accessed from, who can potentially access it, and what has the ability to access it. You can start by making a list of these assets.
The AFCEA has a great diagram of how you might consider scoping assets for CMMC.
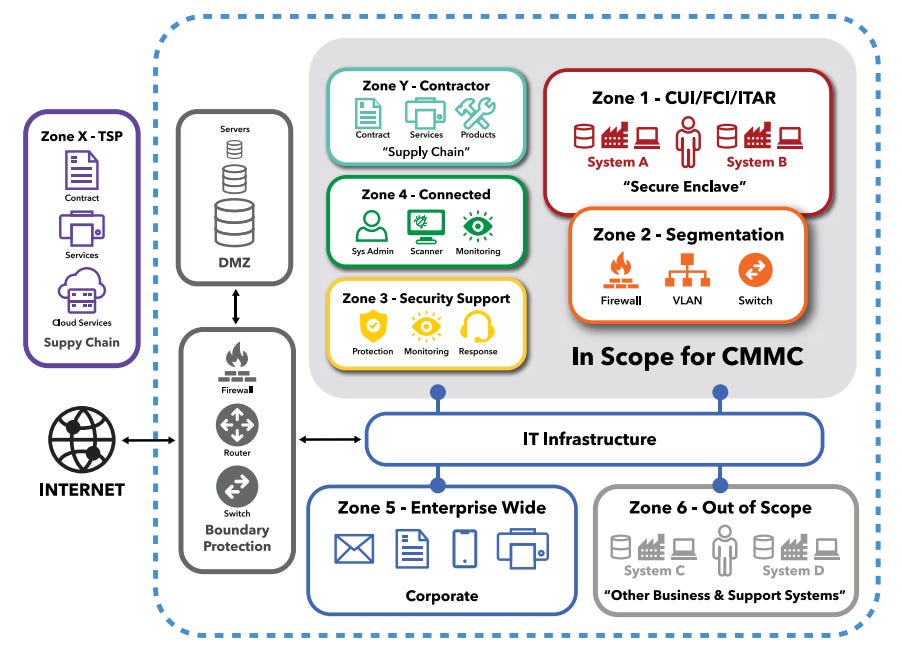
Your operational technology (OT), Internet of Things (IoT) devices, and Test Equipment are not in scope for these controls.
Making Progress
There are many many words written for each of the items in the NIST 800-171 document (and assessment requirements) and CMMC Level 1 Guide. For each of these items, there are simple things you can do to start making progress.
This obviously isn’t a replacement for a thorough self-assessment.
1. Limit All Access to Authorized Users Only

Only people who actually need access to government contract info should have it. Start by restricting access now, not later.
Quick Wins - Set up groups in Active Directory or SharePoint for departments that handle federal information and assign users to these groups. Keep it high level. Then remove access when they leave or roles change. Create a quarterly meeting reminder to review these groups for accuracy.
2. Limit Access to Authorized Departments Only

Even if someone has access to files, they should only be able to do what their job requires—nothing more.
Quick Win - Assign roles within Active Directory or SharePoint that restrict what each group can do, like read-only or edit access, but no deletion rights.
3. Control Access To and From External Connections

Make sure only authorized people and devices connect to your systems and that external systems and websites storing sensitive info are protected.
Quick Wins - Disallow personal devices from accessing company information, or use Conditional Access Policies and Mobile Device Management solutions to protect info. Inventory systems, vendors, and platforms. Look at router and firewall connections to ensure only trusted devices and destinations are allowed.
4. Be Careful with Public Posts and Website Files

Don’t let sensitive contract information reach the public. Policies should dictate who can share things online, on third-party websites and forums, and ensure they’re reviewed before and after.
Quick Wins - Write down who can post contract-related information online and a verification process before information relating to a contract is shared or posted.
5. Every User Gets Their Own Login

Every user must have their own login, and all logins should be logged and monitored.
Quick Win - Get rid of shared accounts. Everyone has their own account on everything.
6. Everything Has a Strong Password

Strong passwords aren’t optional. Make sure you’re using unique passwords and follow NIST guidelines.
Quick Wins - Enforce a policy requiring 14-character unique passwords across all systems handling federal information or hardware-backed PINs or biometrics. Start with a good password policy on Active Directory accounts. (yes, NIST says 8 characters and 6 digit PINs, but go 14+ and remove the 90 day change requirement).
7. Safely Destroy Computers and Hard Drives and USB Drives

When it’s time to dispose of devices, make sure you safely sanitize or destroy them.
Quick Wins - Follow NIST 800-88 guidelines to ensure secure destruction of USB drives and hard drives before disposal or re-use. Write down when and how this is down.
8. Only Let Escorted and Approved People Access Sensitive Places

Physical access to sensitive areas needs to be locked down and tracked.
Quick Wins - Define who can access areas with sensitive information in a policy. Lock your doors or otherwise restrict access. Use a sign-in and sign-out logbook. Lock your network room. Track where keys and badges are.
9. Protect Networked and Wireless Communications

Create separate networks for sensitive information and control traffic at network boundaries.
Quick Wins - Diagram your internal and external network boundaries - perfection not required. Monitor traffic crossing those boundaries. Restrict ports and isolate inter-device communications.
10. Segment Networks and Systems

Public website servers and guest WiFi access should not be able to directly communicate with internal, non-public systems.
Quick Wins - Use firewall rules, virtual networks, and wireless isolation to limit which devices can communicate with each other.
11. Fix Security Problems

Security flaws are like mold—fix them before they cause irreparable damage.
Quick Wins - Set up a basic process for responding to and, most importantly, resolving security alerts from your antivirus software and employee reports.
12. Install Antivirus on Important Systems

Make sure critical systems have antivirus and firewall protection, and configure automatic scans and cloud-enabled protections.
Quick Wins - Use business-grade Endpoint Detection and Response solutions. “Windows Defender for Business” and Sentinel One are good considerations.
13. Keep Things Updated and Patched

Updates and patches are essential - long gaps between updates and upgrades have been responsible for countless breaches.
Quick Wins - Enable automatic updates on everything you can or unattended upgrades on Linux. Set a patch schedule prioritizing externally facing systems and use the Exploit Prediction Scoring System (EPSS) to prioritize what gets patched.
14. Regularly Scan Systems with Antivirus
Schedule regular antivirus scans and make sure they happen automatically when files are opened or downloaded.
Quick Win - Most respectable security solutions do this by default. Get one.
What Next?
Currently, you’re not required to do more than self-attest at Level One, but it is good practice to add your attestation to SPRS.
You’re also not required to have a System Security Plan (aka Information Security Policy and Procedures), nor do you need Plans of Action and Milestones (POAMs) for remediation, though it is best practice and recommended by the DoD to adopt a plan.
You can start preparing for Level Two by documenting the above and starting with an Information Security Policy or System Security Plan.
This is an evolving space with implications for everyone in the Defense space. It will impact your vendors and managed IT companies and the software platforms you use.
There’s more to come, but you can get started today internally. To help kickstart your security program, you might also be interested in the copy-paste Secure Startup Manifesto and its associated resources, documents, and playbooks.





