In this guide, we’ll answer the following questions and provide a simple questionnaire you can use to assess your own organization.
- An Honest Maturity Assessment: Where Are You Really?
- The Prerequisites Checklist: Are You Ready?
- External Forcing Functions: When You Don’t Get to Choose
- How to Scope Your First Pen Test When Budget is Limited
- When You Can’t Afford It Yet: Alternatives That Can Help
- Making the Right Call
- The Real Answer to “Are We Ready?”
You're sitting on your couch late one evening, and your phone buzzes. Looking down, you see a Slack message from the VP.
“Should we get a penetration test?”
It’s a simple question. But the answer isn’t so black and white.
You could say “yes”, because security is important, right? But if you’re honest, you know your authentication system is held together with duct tape and optimism. You’re shipping features faster than you can document them. Your staging environment is… well, you’ll get to that eventually.
You could say “no”, but then what? The founder just got off a sales call where an enterprise prospect asked for your latest penetration test report. Your investor asked about security during the last board meeting. Your competitor just announced they’re SOC 2 certified.
Here’s what most security vendors won’t tell you: There is a right time for your first penetration test. Too early, and you risk wasting money testing a half-built system that’ll be completely different in three months. Too late, and you’re shipping vulnerabilities to paying customers and scrambling to remediate in production while explaining to angry enterprise prospects why you don’t have a pen test report (or why those vulnerabilities showed up on their due diligence penetration tests).
This article is about finding that sweet spot.
Want help figuring out if you’re ready?
We created a Penetration Test Readiness Assessment—a two-minute self-evaluation that tells you exactly where you are and what your next three security priorities should be.
Take the Readiness Assessment
An Honest Maturity Assessment: Where Are You Really?
Security maturity models for startups are … inspirational. They’re probably written by some enterprise risk team that’s never had to choose between hiring an engineer and buying a security tool. They assume you have a large security team (you don’t), a dedicated compliance person (nope), and a fully documented security program (lol).
Here’s a more honest framework:
Stage 0: Pre-Product (You’re Not Ready)
What it looks like: You’re still building the MVP. Maybe you have a few beta users, maybe just internal testing. Major portions of the codebase might get rewritten next month. You’re deploying to production manually, or your continuous deployment is pure Rube Goldberg. The few developers are 100% focused on product market fit.
Should you pen test? No. But keep reading.
What should you do instead?
- Make sure the devs understand defensive coding practices (use the Open Web App Security Project OWASP guidelines and Application Security Verification Standards)
- Run free automated scanners (ZAP by Checkmarx, SemGrep, Snyk, open source framework security auditors)
- Pre-commit hooks to prevent secrets from entering commit history
- Focus on the fundamentals: be careful about the data you store, get your authorization and authentication right, encrypt all the things, encode all output, etc
Why not pen test now? You’ll spend at least $20K to have someone tell you things you probably already know that will be completely irrelevant in two months. Why would you get a home inspection on a house you’re planning to demolish and rebuild?
Stage 1: First Real Customers (Maybe Ready)
What it looks like: You have some paying customers. You’re handling real user data. Your product architecture is relatively stable. You have a growing number of engineers. Your regular prod builds are slightly less Rube Goldberg-y.
Should you pen test? Maybe. It depends on three things.
1. What kind of data do you handle?
- Sensitive Personally Identifying Info (PII), Personal Health Info (PHI), Financial Info, Other - Child/Biometrics/Race/Personal Numbers/Geolocation/etc → You probably should
- Basic personal information, aggregate, anonymous data → You can probably wait
2. Who are your customers?
- Other startups/SMBs → You can probably wait
- Enterprise buyers → They’re going to ask for it soon
3. What’s your runway?
- Less than 6 months → Prioritize survival over pen testing
- 12+ months → Consider it, especially if it unblocks deals
The alternative: Get a security architecture review instead. It’s cheaper ($5K-$10K), catches architectural issues before they’re baked in, and gives you a roadmap of what to fix before a pen test. Think of it as pre-pen-test prep.
Stage 2: Product-Market Fit (Probably Ready)
What it looks like: You have 10-20 major customers. You’re adding features, and the core product is stable. You have 10 to 50 employees. You’re thinking about Series A or just raised it. Your biggest deals are starting to ask harder, invasive security questions you can’t answer with confidence.
Should you pen test? Yes. But only if you pass the readiness checklist below.
Why now?
- You’re at the point where vulnerabilities have real business consequences
- Enterprise prospects are asking for pen test reports
- You’re stable enough that findings will stay relevant for 6-12 months
- You (hopefully) have budget and the sprint space to remediate what they find
Stage 3: Scaling Revenue (Definitely Ready)
What it looks like: You have hundreds of customers. You’re pursuing or have achieved SOC 2 and other robust compliance frameworks. You have enterprise deals in your pipeline. You’re hiring a dedicated security person (or already have one). You’re Series A or B funded.
Should you pen test? Absolutely. If you haven’t already, you’re behind.
Why it’s non-negotiable now:
- Enterprise security questionnaires ask for recent pen test results
- Investors doing due diligence will expect it
- Your competitors are doing this and use it to win deals
- A significant breach at this stage could be existential
- Compliance frameworks strongly suggest it (and PCI, FedRAMP, FTC Safeguards require it)
The Prerequisites Checklist: Are You Really Ready?
If you’re not ready, that penetration test will be a waste of money. You’ll learn little new, and the results won’t be valid for long. Before you schedule one, honestly assess whether you have these basics in place:
1. Someone on your team can fix what they find
This sounds obvious, but it’s a far too common mistake.
- A pen test will generate a report with say 10-40 findings. Roughly:
- 2-5 critical or high-severity issues that need fixing immediately
- 8-15 medium severity issues that need addressing within 30-90 days
- 10-20 low/informational findings that are eventual fixes
Someone needs to:
- Understand the findings
- Translate them into actionable tickets for developers
- Prioritize what gets fixed and in what order
- Fix them
- Verify the fixes work
If your entire engineering team is underwater shipping features and you have no security expertise, you’ll get a pen test report that sits in Google Drive forever, and nothing will get fixed. Hopefully that potential customer doesn’t ask for a remediation validation document.
Minimum viable team:
- At least one senior engineer who understands security concepts
- Engineering capacity to dedicate several weeks to remediation work
- An engineering leader who will prioritize security fixes over feature work
2. You have basic security hygiene in place
Don’t pay for a pen test to tell you things you should already know. If you can’t do a single push-up, you don’t need a personal trainer to tell you that you should, with info you can get from a YouTube video.
Basics you should have before a pen test:
Threat Modeling
- Define what should be tested and why
- Ask what you’re confident about (and check that assumption)
Authentication & Authorization
- You use a standard authentication library or service, not homegrown crypto
- You’ve thought through authorization and it’s applied consistently
- Session management exists and tokens eventually expire
- Users can only access their own data (you’d be surprised how many MVPs fail this)
Data Protection
- Sensitive data is encrypted at rest (at minimum: passwords, tokens, API keys)
- All connections use HTTPS/TLS
- You’re not logging sensitive information in plain text
Input Validation
- User input is validated, sanitized, and encoded before being output
- You use parameterized queries (no raw SQL string concatenation)
- File uploads have type and size restrictions
Basic Monitoring
- Logging exists for authentication, authorization, data access, data change events
- You’d notice if someone was actively attacking you
Infrastructure
- Your developers don’t all have root AWS access
- Your env variables and secrets aren’t scattered everywhere
- You’ve run a platform security audit tool to fix low hanging fruit
How to assess this: See tasks from Stage 0 - run automated scanners and audit tools. If they find critical issues, fix those before paying for human testers.
3. You have budget - not just for the test, but for fixing what they find
The pen test is the cheap part. The expensive part is remediation.
Budget breakdown for your first pen test:
The pen test itself: $15K - $35K+
- Small/focused scope: $15K - $20K+
- Medium scope (web app + API): $20K - $30K+
- Comprehensive (web + API + mobile + infrastructure): $30K - $50K+
And remediation work: $20K - $60K in engineering time
- 2-4 weeks of engineering time (depending on findings)
- Possible infrastructure changes (security tools, architecture updates)
- Re-testing: $3K - $8K (to verify fixes work - ask your pen test partner if it’s included)
Total first pen test cost: $20K - $50K plus another $10K - $50K in time
If you only have budget for the test but not the fixes, reconsider. A report full of unaddressed vulnerabilities could be worse than no report at all - at least ignorance is defensible. Willful negligence is not. We’ve created a basic calculator for ballpark pricing here.
4. Your product is stable enough that findings will be relevant beyond next week
If you’re planning a major architecture rewrite, migrating to a new auth system, or fundamentally changing how data flows through your application in the next few sprints, wait until after that’s done.
Bad timing examples:
- “We’re about to migrate from monolith to microservices” Wait
- “We’re rebuilding our entire frontend in React” Probably wait
- “We’re moving from Auth0 to a homegrown system” Definitely wait (and maybe reconsider that decision)
Good timing examples:
- “Our core product is stable, we’re just adding features” Good time
- “We just finished a major migration and have stabilized” Good time
- “We’re about to pursue SOC 2 and need a baseline” Good time
5. You have a staging or testing environment
Don’t test in production for your first pen test unless you can be absolutely certain the actions taken won’t be seen by other tenants. Why? Pen testers try to break things. Granted, no one should be trying to bring down your service or DDoS your infrastructure. But fuzzing inputs, weird forms, and cache testing might affect clients.
Note that many mature companies do test in production with appropriate controls: isolated tenants, robust performance capabilities, reasonable confidence in their technology stack.
What does “staging environment” really mean?
- Separate infrastructure from production
- Contains realistic test data (not production data!)
- Mirrors production architecture closely enough that findings are relevant
- Can be broken without affecting real customers
Can’t afford a staging environment (due to either time or money)? Your penetration test might be scoped in a way that you’re not getting the full value out of it and you risk impacting customers. You may or may not be ready for a pen test yet.
External Forcing Functions: When You Don’t Get to Choose
Sometimes the decision isn’t about readiness. Sometimes the decision is made for you.
1. Enterprise Sales Deal
The trigger: You get a security questionnaire with 150 questions, including “When was your last penetration test?” and “Can you provide the most recent pen test report?”
Timeline: They want to close by end of quarter. That’s 6 weeks away.
What to do:
- Be honest with the prospect: “We haven’t completed a penetration test yet, but we’re scheduling one now.”
- Ask if they’ll accept a scope definition and scheduled test date to move forward
- Get a pen test scheduled ASAP (even if you’re not perfectly ready)
- Prioritize getting it done over getting perfect results
Pro tip: Ask if your prospect will accept a pen test in progress with a commitment to share results within 30 days of completion. The fact that you’ve engaged a firm shows you take security seriously.
2. Series A Due Diligence
The trigger: Your term sheet comes with due diligence requirements. The investor’s technical advisor wants to review your security posture.
Timeline: You have 30-60 days before funding closes.
What to do:
- If you have a recent pen test (less than 12 months old), great—share it and show how you’ve addressed findings
- If you don’t have one, be upfront: “Security testing is on our immediate post-funding roadmap”
- Have a plan: Show them you understand your security posture and have a roadmap
- Consider getting a rapid third-party security architecture audit and review to show you’re serious
Reality check: Most Series A investors won’t require a pen test for funding, but they’ll expect you to do one soon after. If you’re in healthcare, fintech, or handling sensitive data, they might require it.
How to Scope Your First Pen Test When Budget is Limited
You’ve decided you’re ready. You have a $30K budget. What should you test?
People make two mistakes here:
1. Testing too much → They try to test everything, testers do shallow work, you get more findings but might be missing the few that require some more thought and time
2. Testing too little → They test only public-facing endpoints with limited privileges, and miss where all the real risk is
Smart approach: Focus on the crown jewels.
Priority 1: Whatever touches customer data
Start with the parts of your application that:
- Store or process sensitive customer data
- Handle authentication and authorization
- Process payments or financial transactions
- Contain customer PII/PHI/etc
For most SaaS products, this means:
- Core web application (authenticated user flows)
- API endpoints that serve customer data
- Admin interfaces
Priority 2: External-facing attack surface
If you have budget left, expand to:
- Public-facing infrastructure (exposed services, ports, etc.)
- Public API endpoints
- Marketing website and blog, if infrastructure is shared with customers
Priority 3: Internal attack surface
For most startups, you can wait on this until you’ve gone through some penetration test iterations.
- Internal tools and admin panels
- CI/CD pipeline security
- Cloud infrastructure configuration
Exception: If you’re in a particularly high-risk environment or have experienced internal threats, move this to Priority 1. This is where red teams live and how ransomware events occur.
What NOT to include in your first pen test:
- Mobile apps (unless that’s your core product) → Focus on the high-use areas
- Social engineering/phishing tests → Wait until you’re required to or optimizing
- Physical security testing → Unless you’re in a regulated industry, this can wait
- Comprehensive infrastructure review → Focus on the application first unless there are exceptions as mentioned above
How to communicate scope to vendors:
Don’t say: “Test everything” or “Test this one page”
Do say: “We want deep testing of our authenticated web application and customer-facing API, specifically focusing on these 3 specific areas that handle sensitive data”
Don’t say: “We have a $20K budget, what can you do?”
Do say: “Here are our highest-risk areas. Given a $20K budget, what depth of testing can you provide, and what would we need to defer to a future engagement?”
Want help figuring out if you’re ready?
We created a Penetration Test Readiness Assessment—a two-minute self-evaluation that tells you exactly where you are and what your next three security priorities should be.
Take the Readiness Assessment
When You Can’t Afford It Yet: Alternatives That Can Help
Let’s be real: You might not have five figures lying around for security testing. Especially if you’re pre-Series A, bootstrapped, or running on fumes.
Here’s what you can do instead:
1. Security Architecture Review ($-$$, 000)
What it is: A security expert reviews your architecture, tech stack, and key code patterns. They identify design-level issues before they become implementation vulnerabilities.
When it makes sense:
- You’re pre-product-market fit but handling real data
- You’re about to make major architectural decisions
- You want to fix problems before they’re baked into production
What you get:
- Review of your architecture diagrams and data flows
- Analysis of authentication, authorization, data protection approaches
- Code review of security-critical components
- Prioritized recommendations for improvement
- Key questions about security configurations of platforms
Value: Often more valuable than a pen test at early stages because it helps you build things securely from the start, rather than finding problems after they’re in production.
2. Automated Security Scanning (Free - $$$/month)
Tools your team should be using:
On your code:
- SemGrep (free tier)
- Snyk (free tier for small teams)
- npm audit / pip-audit / cargo audit (free)
- GitLeaks or TruffleHog
On your running web apps:
- Burp Suite Community Edition (free)
- ZAP by Checkmarx
- Framework security auditors
On your infrastructure:
- ScoutSuite, Prowler, etc (free, cloud security auditing)
- Other open source platform security auditors
- Cloud provider native tools (AWS Security Hub, Azure Security Center)
Automated tools find maybe a fraction of what human testers find. But that fraction includes the low-hanging fruit that you absolutely should fix. Think of it as security hygiene, not comprehensive testing.
3. Bug Bounty Programs (Variable cost)
When it makes sense:
- You’ve fixed all the obvious issues (run automated scanners first)
- You’re comfortable with public disclosure of your security program
- You can respond to reports within 24-48 hours
- You have budget to pay researchers for valid findings
Options:
- Self-hosted (security.txt + responsible disclosure page) - Free
- HackerOne / Bugcrowd - Platform fee + bounty payments
- Private programs - Only invited researchers
Warning: Don’t start a bug bounty if you can’t handle the influx. There will be many, many poorly written, false-positive, and AI-generated reports. But there will be signal in the noise.
4. Fractional Security Advisor ($-$$,000/month)
Somewhere between “can’t afford a dedicated security role” and “need ongoing security and compliance guidance” is the fractional security advisor, aka vCISO.
What you get:
- Several meetings and emails per month with expert security resources
- Architecture reviews for new features
- Security questionnaire support
- Vendor evaluation
- Incident response planning
When it makes sense:
- Security questions are blocking deals
- You’re pursuing compliance (SOC 2, ISO 27001, etc)
- You can’t justify a full-time hire yet
Ask your network for references and interview for fit, understanding of your business, and relevant experience. The best vCISOs act as advisors with technical, compliance, and policy experience - not as sales channels.
Making the Right Call
Here’s a decision tree to make this more concrete.
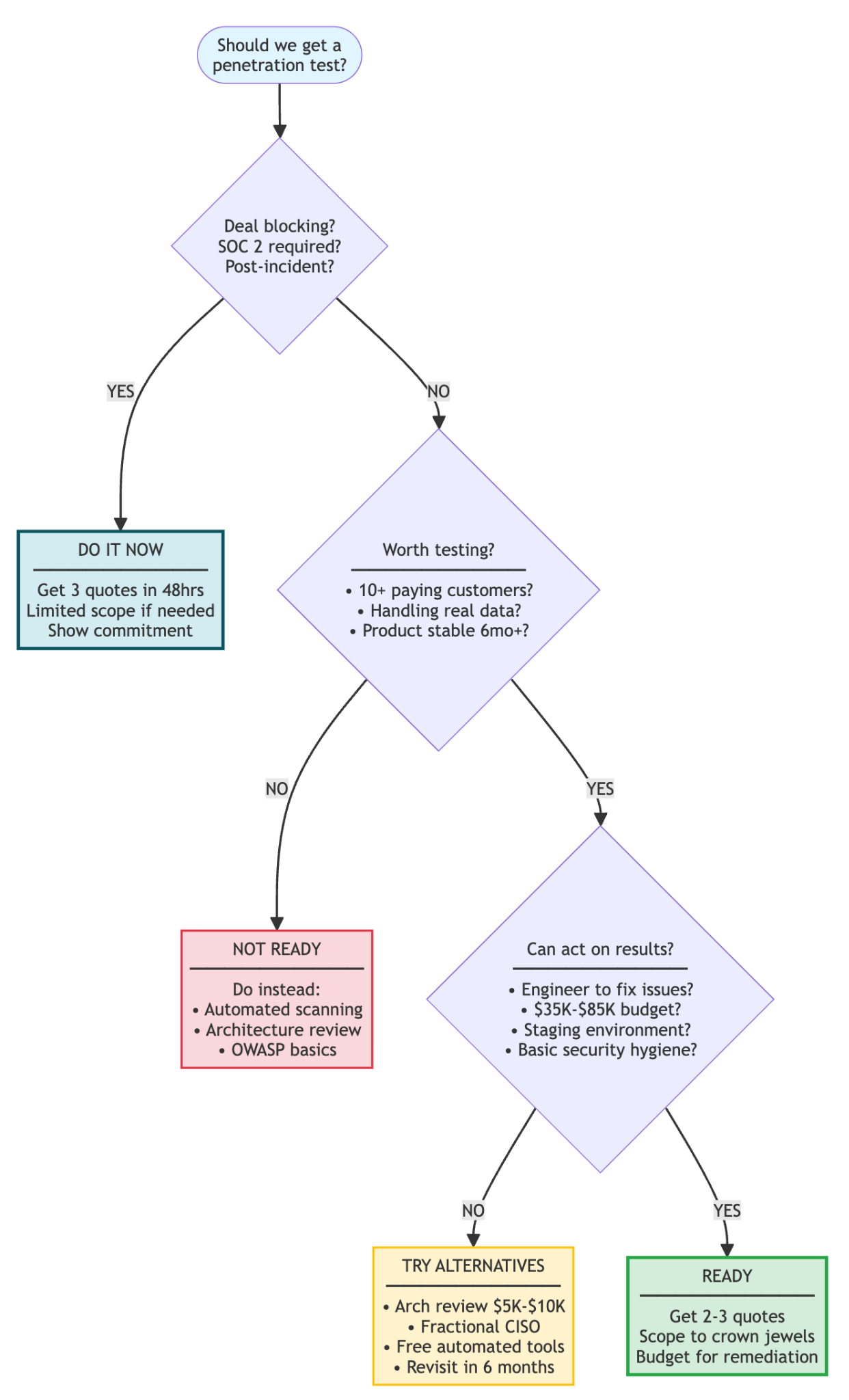
The Real Answer to “Are We Ready?”
If you made it this far, you already know the answer. You’re ready for a penetration test when:
- You have something worth testing (stable product, real customers, real data)
- You can act on the results (team capacity, budget for fixes, staging environment)
- The timing makes business sense (before an important deal, during compliance, after stabilization)
If you check all three boxes, schedule it. If you check zero boxes, wait and focus on the basics. If you check one or two boxes, it’s a judgment call. Reading this means you’re erring on the side of caution, which is the right instinct.
The worst decision is doing nothing because you can’t decide. The second-worst decision is doing a pen test you’re not ready for. The best decision is to be honest about where you are and make a plan to get where you need to be.
So: Are you ready?
Want help figuring out if you’re ready?
We created a Penetration Test Readiness Assessment—a two-minute self-evaluation that tells you exactly where you are and what your next three security priorities should be.
Take the Readiness Assessment
About This Series
This is Part 0 of our Strategic CISO Series—a collection of guides focused on turning operational security work into strategic wins.
Read the series:
- Part 0: Before the Test: When Your Startup is Ready for Penetration Testing (you are here)
- Part 1: Timing Your Security Assessment for Executive Impact
- Part 2: How to Say ‘We Need More Security Budget’ Without Saying ‘We’re Currently Insecure’
- Part 3: The Pre-Mortem Pen Test: Using Security Assessments to Accelerate M&A, Funding, or Major Launches
- Part 4: From Checkbox to Competitive Advantage: Positioning Your Security Posture Externally
- Part 5: The Quarterly Security Win: Manufacturing Visible Victories When Your Job Is Preventing Invisible Disasters
Written for security leaders who understand that doing security right means knowing when to wait as much as knowing when to act.





