They’re not hacking you - they’re just walking through your front door. IT Directors at accounting and professional services firms face a sophisticated, persistent threat actor specifically targeting their industry.
TA4903, a Nigerian-origin cybercrime group active since 2019, has stolen millions through credential phishing and business email compromise campaigns that bypass traditional MFA.
The average business email compromise (BEC) incident costs a median $80,000 up to $4.88 million, making up the majority of cyber incidents in recent years. Professional services firms were targeted in nearly a third of Q1 2025 phishing campaigns—making you a primary target.
This matters because TA4903 combines high-volume credential theft with targeted follow-on fraud, searching compromised mailboxes for payment information within six days and executing wire transfer fraud through supplier impersonation. The group uses EvilProxy, a phishing-as-a-service toolkit that intercepts session cookies to bypass SMS codes, authenticator apps, and push notifications—the MFA methods most firms rely on.
TA4903 evolved from simple government agency spoofing in 2021 to sophisticated attacks using QR codes in PDFs, HTML attachments, and SMB impersonation with “cyberattack” themes requesting banking updates. The operational tempo increased sharply in mid-2023, with campaigns targeting construction, manufacturing, finance, healthcare, and specifically accounting firms handling sensitive financial transactions.
With over 1 million EvilProxy attacks detected monthly in 2024 and TA4903’s proven track record of mailbox infiltration leading to multi-hundred-thousand-dollar fraud, the question isn’t whether your firm will be targeted—it’s whether your current defenses will stop them.
Understanding the TA4903 threat actor and operational model
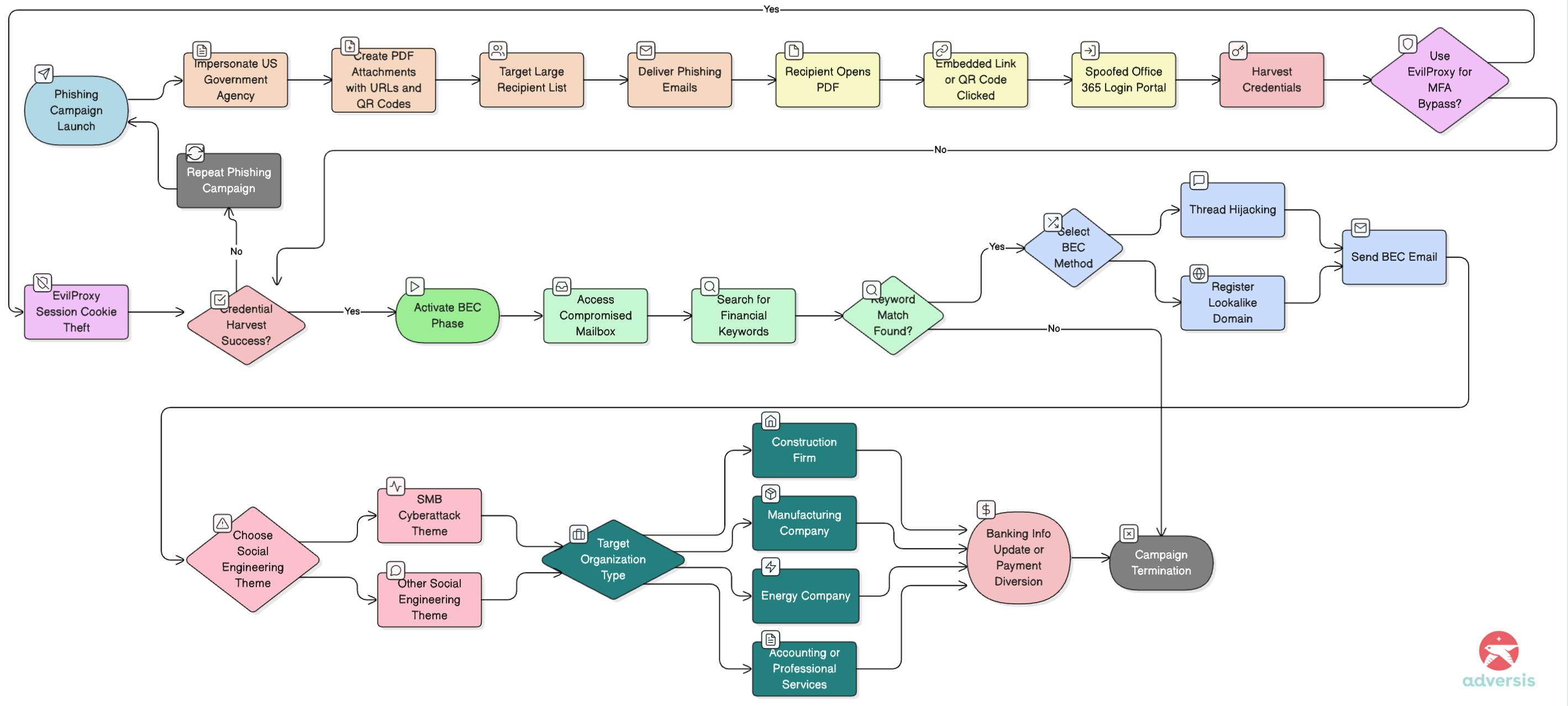
TA4903 operates a dual-objective criminal enterprise combining mass credential phishing with targeted business email compromise. Proofpoint researchers identified the group through consistent PDF metadata (author name “Edward Ambakederemo”), domain construction patterns, and behavioral clustering across campaigns dating to December 2021, though broader activity traces to 2019. The group is assessed with high confidence to be Nigerian in origin based on naming conventions, BEC methodologies, and operational patterns.
The operational model works in two phases.
First, high-volume phishing campaigns impersonate legitimate U.S. government agencies (USDA, Department of Transportation, Department of Labor, Small Business Administration) with fake bid proposals delivered via PDF attachments containing embedded URLs and QR codes.
These campaigns target hundreds to tens of thousands of recipients, capturing corporate Office 365 credentials through spoofed login portals. Throughout 2023, TA4903 subscribed to EvilProxy for approximately $400 per month, enabling bypass of multi-factor authentication through session cookie theft. While EvilProxy usage declined in late 2023, the infrastructure investment demonstrates financial sophistication and willingness to adopt advanced techniques.
The second phase activates within six days of credential theft. In controlled honeypot testing, Proofpoint researchers observed TA4903 accessing compromised mailboxes and searching specifically for keywords including “bank information,” “payment,” and “merchant.”
The actors then pivot to business email compromise using either the compromised account directly (thread hijacking) or newly registered lookalike domains spoofing suppliers and business partners. Starting in May 2023, TA4903 shifted emphasis toward SMB impersonation with “cyberattack” themes—fraudulent emails claiming the sender’s company was breached and requesting immediate banking information updates. This social engineering tactic proved highly effective, with BEC operational tempo exceeding credential phishing campaigns through 2024.
TA4903’s targeting is sector-agnostic but shows particular focus on organizations handling financial transactions: construction firms managing project payments, manufacturing companies with complex supply chains, energy companies with large vendor networks, and critically, accounting and professional services firms serving as financial intermediaries for clients. The group’s evolution from straightforward government spoofing to sophisticated multi-stage attacks with QR codes, HTML attachments, and selective exploitation of high-value targets demonstrates intermediate-to-high sophistication and operational adaptability.
How EvilProxy reverse proxy architecture defeats your MFA
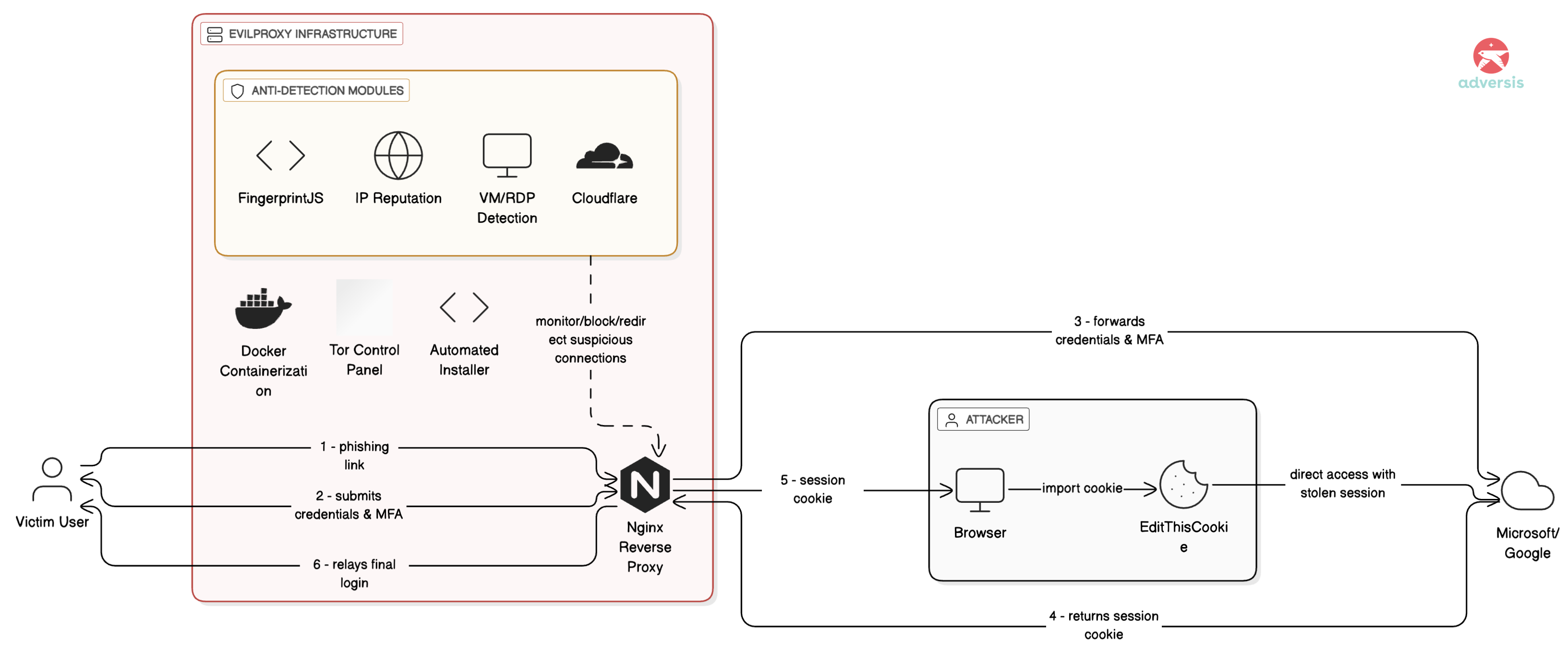
EvilProxy represents a fundamental shift in phishing technology by implementing adversary-in-the-middle attacks through transparent reverse proxy architecture. Unlike traditional phishing that clones login pages and simply harvests credentials, EvilProxy creates real-time bidirectional communication between the victim and the legitimate Microsoft, Google, or other cloud service. This architectural approach defeats multi-factor authentication not by breaking the cryptography but by stealing the authenticated session itself.
The technical mechanism works as follows. When a victim clicks a phishing link, they connect to an EvilProxy-controlled nginx server configured as a reverse proxy. This server dynamically fetches the legitimate login page content from Microsoft or Google in real-time, displaying authentic branding, valid SSL certificates from Let’s Encrypt, and even the correct URL structure to the victim. As the victim enters credentials, the proxy forwards these to the legitimate service. When Microsoft or Google challenges for the second factor—SMS code, authenticator app OTP, or push notification—the proxy displays this challenge to the victim who believes they’re interacting with the real service. Upon successful MFA completion, the legitimate service returns a session cookie containing authentication tokens. EvilProxy intercepts this cookie before relaying the final authentication back to the victim.
The attacker now possesses a valid session cookie that remains active for hours or days depending on service configuration. By importing this cookie into their own browser using tools like EditThisCookie, the attacker accesses the victim’s account without needing credentials or MFA—the session is already authenticated. Microsoft’s .AspNet.Cookies and similar session identifiers cannot distinguish between the legitimate user’s session and the attacker’s stolen cookie because they’re cryptographically identical. This is why EvilProxy bypasses SMS codes, authenticator app OTPs, push notifications, and even number-matching challenges. All these methods occur before session cookie issuance and therefore provide zero protection against session hijacking.
The EvilProxy infrastructure uses Docker containerization for rapid deployment, with customers receiving SSH access and automated installation scripts. The service operates through Tor-hosted control panels at .onion domains, with Telegram serving as the primary business channel under administrator “John_Malkovich.” Pricing is service-specific: $150-$400 for 10-31 days targeting Microsoft services, $250-$600 for Google services. The platform includes anti-detection features such as bot fingerprinting using the open-source FingerprintJS library, IP reputation analysis blocking VPNs and Tor exit nodes, virtual machine detection, RDP connection blocking, and Cloudflare integration for traffic disguising. When suspicious activity is detected, the proxy either drops the connection or redirects to benign sites.
EvilProxy’s effectiveness is evidenced by Proofpoint’s detection of over 1 million attacks monthly as of 2024. The service democratizes sophisticated attack techniques previously limited to advanced persistent threat groups, making MFA bypass accessible to low-skill cybercriminals for a modest subscription fee. This commoditization of adversary-in-the-middle attacks fundamentally challenges the security assumption that MFA provides adequate credential protection—it doesn’t, unless you deploy phishing-resistant authentication.
Why your current MFA fails and what actually works
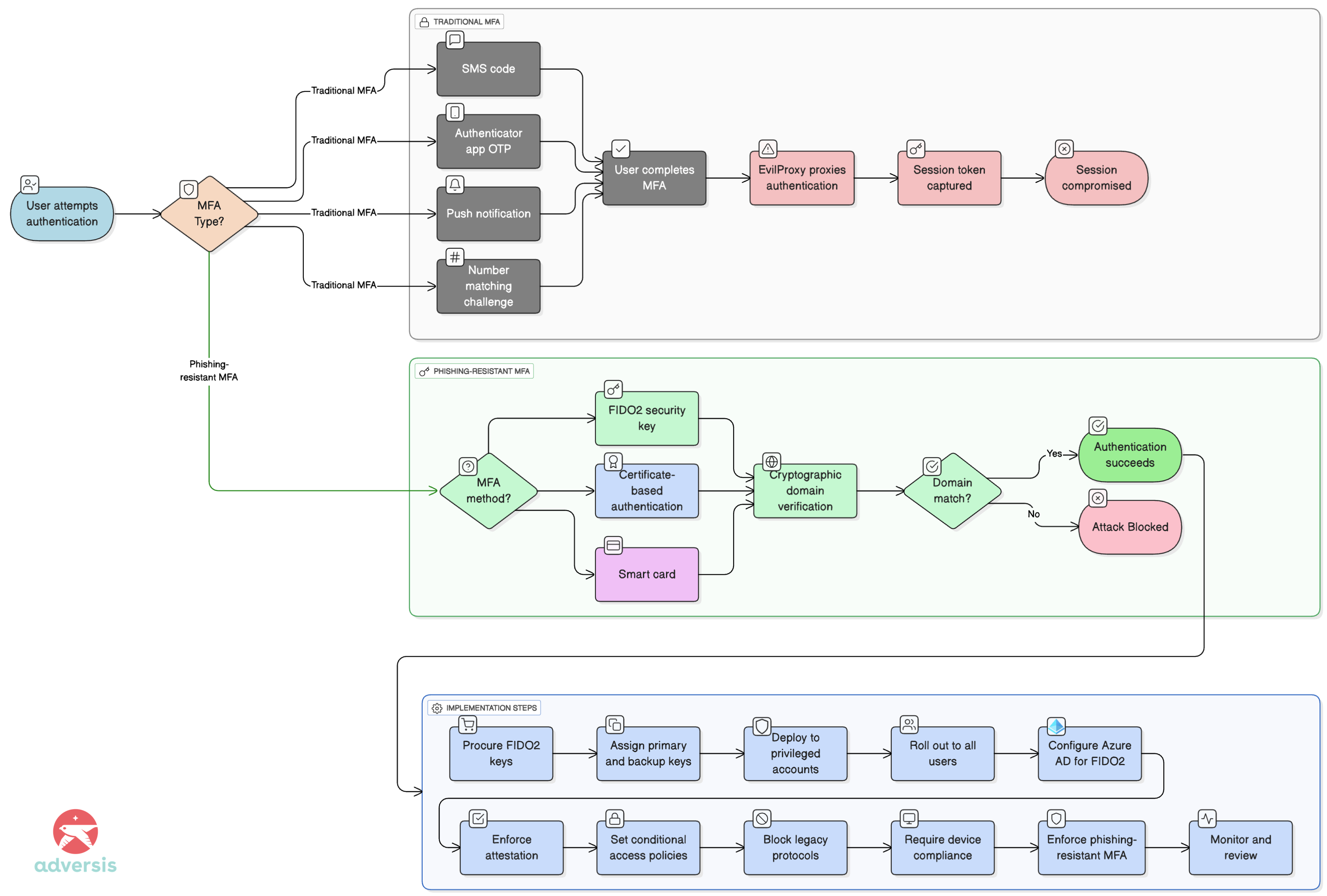
The MFA methods most accounting firms currently deploy are vulnerable to EvilProxy because they authenticate the user but not the origin. SMS codes, authenticator app one-time passwords, push notifications, and even number-matching challenges all occur during the authentication process that EvilProxy proxies in real-time.
The victim completes legitimate MFA with the legitimate service—EvilProxy simply captures the resulting authenticated session. This is not a weakness in MFA implementation but an architectural limitation of knowledge-based and possession-based factors that don’t verify the domain origin.
Phishing-resistant MFA uses public key cryptography tied to the origin domain. FIDO2 security keys (hardware tokens like YubiKey, Token Ring, or Feitian devices) implement WebAuthn protocol, where the browser and authenticator cryptographically verify the domain URL before completing authentication.
When a victim attempts to authenticate to a phishing site with a different domain than the legitimate service, the cryptographic challenge fails because the domain doesn’t match. EvilProxy cannot proxy this cryptographic verification because it requires the attacker to possess the legitimate domain’s private key—which is mathematically infeasible. This is why FIDO2 keys provide 99.9% protection against phishing versus 40-60% for traditional MFA methods.
For accounting firms, the implementation path is straightforward. Purchase two FIDO2 security keys per user for redundancy—primary and backup.
Budget options like Identiv uTrust FIDO2 cost $14-25 per key; mid-range options like Feitian BioPass cost $25-35; enterprise YubiKey 5 series cost $45-50. Deploy to privileged accounts (admins, partners, anyone with financial system access), then roll out organization-wide in a phased approach.
The technical configuration in Azure Active Directory requires enabling FIDO2 as an authentication method and optionally enforcing attestation to prevent rogue security keys. Configure conditional access policies requiring phishing-resistant MFA for all cloud applications, particularly Office 365, accounting software, and client management systems.
Block legacy authentication protocols entirely—Exchange ActiveSync, IMAP, POP3—which cannot support modern authentication. Implement device compliance requirements so only managed, up-to-date devices access corporate email. These controls work in concert: FIDO2 prevents credential theft, conditional access prevents session abuse, and device compliance ensures endpoint security.
The critical mistake is making phishing-resistant MFA optional. When traditional MFA methods remain available, users choose convenience over security, and attackers simply wait for users on less-secure methods.
Google, Twitter/X, Discord, and Cloudflare all mandated security keys for all employees after realizing that optional deployment provided insufficient protection. Your implementation must enforce phishing-resistant MFA for at minimum all finance personnel, executives, IT administrators, and anyone handling client financial data.
Recognizing these campaigns targeting your firm
TA4903 phishing campaigns exhibit consistent patterns enabling proactive detection. Government-themed campaigns impersonate federal agencies with subject lines containing “Invitation To Bid,” “RFP,” or “Government Contract Opportunity” The sender domain follows a predictable pattern: government agency acronym plus “bids” or “bid” (example: tender-usdabids[.]com, index-dolbid2024[.]com). These domains are typosquatted variations of legitimate .gov domains but registered as .com, .net, or .bid TLDs. The emails contain multi-page PDF attachments with professional branding mimicking USDA Agricultural Marketing Service, Department of Transportation procurement offices, or Department of Labor contracting divisions.
The PDF metadata consistently shows author name “Edward Ambakederemo”—a signature that email security gateways can flag. Inside the PDFs, both embedded hyperlinks (“Click here to submit bid”) and QR codes redirect to the same credential phishing destination.
The QR codes appeared in late 2023 as an evasion technique since traditional email security cannot analyze image-embedded codes. Mobile users scanning these codes on smartphones bypass desktop email protections and face smaller screens making fake login pages harder to scrutinize.
The phishing landing pages are direct clones of Microsoft Office 365 login portals with valid SSL certificates and professional appearance.
SMB-themed campaigns shifted tactics in mid-2023 toward supplier and vendor impersonation. These emails spoof known business partners with subject lines like “Payment Remittance Update,” “New Receipt from Finance Department,” or “URGENT: Banking Information Change Due to Cyberattack” The “cyberattack” theme proved particularly effective—fraudulent emails claim the sender company suffered a breach requiring immediate banking detail updates for pending payments.
This social engineering combines urgency, fear, and legitimate business context to pressure accounts payable personnel into compliance. The spoofed domains often contain spelling errors (one letter off legitimate domains) or added elements like “llc” or “inc” (example: spoofing acmesupply[.]com with acmesupplyinc[.]com).
Thread hijacking represents the most sophisticated variant. After compromising a corporate mailbox, TA4903 monitors existing email conversations between the victim organization and its vendors or clients. The attacker inserts themselves into legitimate threads with messages like “Please note our updated banking details for the attached invoice.” Because the email originates from a compromised legitimate account and continues an existing conversation, traditional security controls fail to flag it as malicious. This technique particularly targets accounting firms managing client funds, where invoice processing often occurs via email.
Detection opportunities exist at multiple layers. Email gateways should flag newly registered domains or closely resembling known vendor domains. PDFs with embedded QR codes warrant automatic sandboxing and OCR analysis to extract destination URLs. Emails requesting banking changes should trigger automatic quarantine pending human review.
Authentication failures on DKIM or DMARC checks indicate spoofing attempts. Azure AD sign-in logs showing impossible travel (authentication from distant locations within physically impossible timeframes), User-Agent switching (same session showing different browsers or devices), or SessionId persistence across multiple IP addresses all indicate session cookie theft post-compromise.
Specific indicators of compromise for TA4903 include domains
auth01-usda[.]comtender-usdabids[.]comshortsync[.]netorga-portal[.]comindex-dol[.]comindex-dolbid2024[.]com
SHA256 hashes for known malicious PDFs are available through Proofpoint Emerging Threats PRO ruleset, updated weekly with TA4903 domain IOCs. Network detection should alert on connections to newly registered domains containing keywords “bid,” “usda,” “dot,” “dol,” “sba” combined with non-government TLDs. The infrastructure shows consistent use of nginx servers with specific status codes (407 Proxy Authentication Required, 444 Nginx-specific responses) and URI paths like /ests/2.1/content/, /shared/1.0/content/, /officehub/bundles/ associated with EvilProxy deployments.
Email authentication that prevents spoofing
Email authentication protocols—SPF, DKIM, and DMARC—form the foundational defense against domain spoofing, yet many accounting firms deploy them incorrectly or not at all.
SPF (Sender Policy Framework) specifies which mail servers can send email on behalf of your domain.
DKIM (DomainKeys Identified Mail) cryptographically signs outbound messages so recipients can verify authenticity.
DMARC (Domain-based Message Authentication, Reporting and Conformance) tells receiving mail servers what to do when SPF or DKIM checks fail and provides reporting on authentication failures.
Together, these protocols prevent actors from spoofing your domain to your clients, vendors, and internal staff.
SPF implementation requires adding a TXT record to your domain’s DNS specifying authorized sending sources.
For Office 365, the record is v=spf1 include:spf.protection.outlook.com -all.
The -all hard fail instructs receiving servers to reject any email from unauthorized sources. Many firms incorrectly use ~all soft fail, which only flags messages as suspicious rather than blocking them—this is insufficient.
Include all legitimate sources: your email provider, marketing platforms, CRM systems, and any third-party services sending on your behalf. Occasional audits should verify SPF includes only active services, as unused entries expand your attack surface.
DKIM implementation requires configuring your email server to sign outbound messages with a private key, while publishing the corresponding public key in DNS.
For Office 365, enable DKIM signing in the console or with PowerShell: New-DkimSigningConfig -DomainName yourdomain.com -Enabled $true.
This generates two CNAME records (selector1 and selector2) to publish in DNS.
Google Workspace configures DKIM through Admin Console under Apps > Google Workspace > Gmail > Authenticate email.
DKIM signatures prevent message tampering in transit and verify the sender genuinely controls the sending domain.
DMARC implementation should follow a phased approach to avoid blocking legitimate email.
Phase 1 deploys monitoring mode: v=DMARC1; p=none; rua=mailto:[email protected]; pct=100.
Note the p=none. No policy is being enforced. This simply collects authentication reports without affecting delivery. After 30 days analyzing reports to identify legitimate sources failing authentication, proceed to Phase 2 quarantine mode: v=DMARC1; p=quarantine; rua=mailto:[email protected]; pct=100.
This sends failing messages to spam folders. After another 90 days confirming no legitimate email is quarantined, advance to Phase 3 reject mode: v=DMARC1; p=reject; rua=mailto:[email protected]; pct=100; adkim=s; aspf=s.
The reject policy instructs receiving servers to block spoofed messages entirely. The adkim=s and aspf=s flags enforce strict alignment, requiring exact domain matches for DKIM and SPF.
DMARC reports arrive as XML attachments detailing every authentication attempt against your domain. Services like dmarcly.com, dmarcian.com, or Valimail parse these reports into human-readable dashboards showing authentication pass rates, failing sources, and potential spoofing attempts.
Target 99% pass rates— lower indicates configuration issues or unauthorized senders. Organizations without DMARC enforcement remain vulnerable to domain spoofing used in TA4903’s government agency and supplier impersonation campaigns.
Complementary email security includes external email tagging, where messages from outside your organization display [EXTERNAL] or [CAUTION: EXTERNAL EMAIL] in the subject or body.
Office 365 transport rules implement this:
New-TransportRule -Name “External Email Warning” -FromScope NotInOrganization -ApplyHtmlDisclaimerLocation Prepend -ApplyHtmlDisclaimerText “<div style=’background-color:#FFEB9C;padding:10px;border:1px solid #9C6500;’>CAUTION: This email originated from outside your organization. Do not click links or open attachments unless you verify the sender.</div>”.
This visual indicator helps users identify potential phishing even when technical controls miss sophisticated attacks. However, over-reliance on user vigilance is insufficient—technical controls must do the heavy lifting.
Building a layered defense
Defense in depth requires multiple overlapping security controls so single-point failures don’t result in compromise. For accounting firms, the critical layers are email security gateway, endpoint protection, and network segmentation. Identity and access management, monitoring and response, and user awareness follow. Each layer addresses different attack vectors and stages of the kill chain.
Advanced email security gateways augment Office 365’s built-in protections with machine learning, behavioral analysis, and threat intelligence. Microsoft Defender for Office 365 (~$10 per user per month) adds Safe Links that detonate URLs in sandboxes before delivery, Safe Attachments that analyze files for malicious behavior, and anti-phishing policies using machine learning to detect impersonation.
Email gateways like Proofpoint Email Protection and Mimecast Email Security offer similar capabilities with more granular policy controls and threat intelligence feeds. Abnormal Security and Material Security takes a behavior-based approach, learning normal communication patterns to detect anomalies indicative of BEC.
Configure anti-phishing policies aggressively for accounting environments. Set the phishing threshold to Level 2 (Aggressive) rather than Level 1 (Standard). Enable mailbox intelligence to learn communication patterns. Activate impersonation protection for executives, partners, and finance personnel - the platform blocks emails impersonating these users even from legitimate domains.
Enable spoof intelligence to analyze sender reputation. Set the action for high-confidence phishing to “Quarantine message” rather than “Move to Junk” to prevent users from accidentally accessing quarantined threats. For Office 365, access these at Microsoft 365 Defender > Policies > Anti-phishing.
Endpoint protection must extend beyond signature-based antivirus to include behavioral detection, attack surface reduction, and controlled folder access. Windows Defender, included in Windows 10/11, provides limited protection when properly configured, but a business-grade EDR is critical. Enable Network Protection to block connections to malicious domains even if email security misses the initial phishing message.
Enable Controlled Folder Access to prevent ransomware encryption of critical accounting data—designate folders like C:\Accounting and D:\ClientFiles as protected. Configure Attack Surface Reduction rules to block Office applications from creating executable content, a common malware delivery technique.
Set-MpPreference -EnableNetworkProtection Enabled
Set-MpPreference -EnableControlledFolderAccess Enabled
Add-MpPreference -ControlledFolderAccessProtectedFolders “C:\Accounting”,”D:\ClientFiles”
Add-MpPreference -AttackSurfaceReductionRules_Ids BE9BA2D9-53EA-4CDC-84E5-9B1EEEE46550 -AttackSurfaceReductionRules_Actions Enabled
Commercial EDR platforms like CrowdStrike Falcon, SentinelOne, or Microsoft Defender for Endpoint (check out Defender for Business for a low-cost option) provide superior visibility and threat hunting. These platforms detect post-compromise activities like unusual process execution, lateral movement attempts, and data exfiltration—critical for catching attacks that bypass email security.
An often-de-prioritized but critical control is network segmentation, which isolates finance and accounting functions from general corporate network access. Create a dedicated VLAN for finance team devices with access control lists permitting only necessary services. Finance systems like QuickBooks, Bill.com, or client portals should reside in this VLAN with firewall rules blocking inbound and lateral movement. This containment limits damage if a phishing compromise occurs outside the finance team—the attacker cannot pivot to financial systems.
Conditional access policies enforce contextual access controls beyond simple authentication. In Azure AD, create policies requiring phishing-resistant MFA for all privileged accounts, blocking access from high-risk countries where your firm doesn’t operate, requiring compliant managed devices for cloud application access, and enforcing sign-in frequency (example: 8 hours for admins, requiring re-authentication multiple times per day).
Block legacy authentication protocols entirely—Exchange ActiveSync, IMAP, POP3, SMTP AUTH—as these cannot support modern MFA and represent persistent vulnerabilities.
Create a break-glass emergency admin account exempt from conditional access, stored securely, to prevent lockout scenarios. Store in a password manager.
Security Information and Event Management (SIEM) aggregates logs from email gateways, identity providers, endpoints, firewalls, and cloud applications for correlation and alerting. Microsoft Sentinel (pay-as-you-go, typically $200-500 per month for small firms) integrates natively with Azure AD and Office 365, providing pre-built analytics rules for TA4903 TTPs. Splunk Cloud and Elastic Cloud offer similar capabilities with different pricing models. Wazuh and other open source alternatives also exist. The value of SIEM is correlation—detecting impossible travel by comparing Azure AD sign-in locations, identifying session hijacking through SessionId anomalies, and alerting on inbox rule creation immediately after suspicious authentication.
Conduct security awareness training for all staff, specifically focused on these tactics. Show actual examples of government bid proposal phishing, QR code PDFs, and cyberattack-themed BEC emails. This session should communicate three messages
- These attacks specifically target our industry
- They are sophisticated and realistic
- Reporting suspicious emails immediately via [email protected] is the right response.
Establish a no-blame culture where even accidental clicks result in assistance rather than punishment—fear of consequences causes underreporting of incidents, preventing timely response.
Continuous security awareness training using a platform like KnowBe4, Proofpoint Security Awareness, or Hoxhunt are okay options. These platforms send monthly simulated phishing campaigns modeled after real-world attacks, provide just-in-time training for users who click, and track behavior change over time. Configure simulations to specifically mimic fraud tactics: government bid proposals with QR codes, supplier emails requesting banking changes, and invoice thread hijacking. Consider bringing in an expert for live or story-based demos and training for better retention. The goal is not to catch and shame users but to change behavior through repetition and education. It’s unlikely you’ll ever have 0% clicks, but ideally shouldn’t go over 3%.
Document incident response procedures - what to do when a user reports a phishing email, how to respond to suspected account compromise, and when to engage external assistance. Test these procedures quarterly through tabletop exercises where you simulate a TA4903 attack and walk through your response.
Detecting active compromises and responding effectively
Post-compromise detection focuses on identifying attacker activities after initial credential theft. TA4903’s pattern of accessing compromised mailboxes within six days and searching for financial keywords provides specific detection opportunities. Azure AD and Office 365 audit logs contain evidence of these activities when properly monitored.
Inbox rule creation immediately after suspicious authentication is a high-fidelity indicator of compromise. Attackers create rules to auto-forward emails containing financial keywords to external addresses, auto-delete responses that might alert the victim, or hide security notifications. Monitor Office 365 audit logs for New-InboxRule operations:
Search-UnifiedAuditLog -StartDate (Get-Date).AddDays(-7) -EndDate (Get-Date)
-Operations “New-InboxRule”,”Set-InboxRule”
-ResultSize 5000 | Export-Csv C:\AuditLogs\InboxRules.csv
Review this output for rules with suspicious criteria: forwarding to external addresses, moving messages to RSS feeds or deleted items, or filtering by keywords like “invoice,” “payment,” “wire transfer,” or “bank.” Legitimate users rarely create complex inbox rules, making this a low-false-positive indicator.
Unusual mailbox access patterns emerge when TA4903 searches for financial information. Query Exchange Online audit logs for SearchExportDownloadedResults, MailItemsAccessed, and MessageBind operations occurring outside normal business hours or from unusual locations. High volumes of rapid folder access, particularly to Sent Items and Archived folders, indicate reconnaissance. PowerShell commands to audit mailbox access:
Search-UnifiedAuditLog -StartDate (Get-Date).AddDays(-30) -EndDate (Get-Date)
-Operations “MailItemsAccessed” -UserIds [email protected]
-ResultSize 5000 | Export-Csv C:\AuditLogs\MailboxAccess.csv
When compromise is detected, immediate containment is critical. Revoke all active sessions for the compromised user to terminate attacker access: Get-AzureADUser -ObjectId [email protected] | Revoke-AzureADUserAllRefreshToken. Reset the password to a randomly generated 20+ character string.
Disable the account temporarily: Set-AzureADUser -ObjectId [email protected] -AccountEnabled $false. These actions prevent further attacker access while preserving the account for forensic analysis.
Investigate the scope of compromise by reviewing inbox rules, mail forwarding configurations, OAuth application grants, and MFA method additions.
Remove malicious inbox rules: Get-InboxRule -Mailbox [email protected] | Where-Object {$_.ForwardTo -like “*external*”} | Remove-InboxRule.
Revoke suspicious OAuth consents where attackers granted third-party applications access to mailbox data: Get-AzureADUserOAuthPermissionGrant -ObjectId [email protected].
Check for MFA method manipulation - attackers sometimes add authenticator apps to maintain persistent access even after password resets.
Preserve evidence before remediation erases attacker artifacts.
- Export the compromised mailbox to PST:
New-ComplianceSearch -Name “BEC-Investigation-UserName” -ExchangeLocation [email protected]. - Capture screenshots of malicious inbox rules, suspicious emails, and authentication logs.
- Document the timeline of attacker activities from initial authentication through detected suspicious behavior.
This evidence supports law enforcement reporting through FBI IC3 (ic3.gov), potential cyber insurance claims, and root cause analysis to prevent recurrence.
Recovery requires re-enabling the account with phishing-resistant MFA enforced. If the user previously had SMS or app-based OTP, force enrollment of FIDO2 security keys before re-enabling access. Require MFA re-registration to clear any attacker-controlled authentication methods. Monitor the account closely for 30 days post-recovery, watching for residual access attempts or related compromises of users the victim regularly corresponds with. Work with your legal representation and if appropriate, notify potentially affected parties—if the attacker had time to send BEC emails from the compromised account, contact recipients immediately to invalidate fraudulent requests.
Conduct a post-incident review to identify security gaps. Was the phishing email reported and ignored? Did email authentication fail to block the initial delivery? Was session hijacking detected too slowly? Did the user lack phishing-resistant MFA? Each incident provides lessons to strengthen defenses. Update security awareness training to include the specific attack vector, adjust email security rules based on the phishing characteristics, and if detection takes too long, enhance monitoring rules for faster identification next time.
Real-world outcomes and what actually stops these attacks
Johnson County Schools in Tennessee lost $3.36 million to BEC in 2024 when attackers spoofed Pearson Education requesting updated banking details for a legitimate textbook order. The school district transferred state education funds to an attacker-controlled account. Recovery efforts yielded less than $750,000. The root cause was lack of dual-channel verification—finance personnel processed the banking change request via email without calling Pearson using a known phone number. A simple phone call would have prevented $2.6 million in unrecovered losses.
The Town of Arlington, Massachusetts, lost nearly $500,000 in June 2024 through thread hijacking. Attackers compromised a construction contractor’s email account, inserted themselves into an existing invoice thread, and redirected four payments to fraudulent accounts. Because the emails originated from the legitimate contractor account and continued an established conversation, the town’s finance department didn’t recognize the fraud until the contractor inquired about missing payments weeks later. This attack succeeded despite the town having reasonable security controls because thread hijacking defeats technical defenses—only payment verification procedures catch it.
The Massachusetts Workers’ Union lost $6.4 million when attackers impersonated their investment manager via email, requesting an urgent transfer to a “new account.” The FBI recovered $5.3 million through rapid response, but $1.1 million remains lost. Investigation revealed the union lacked multi-factor authentication on email accounts and had no callback verification procedure for financial requests. Basic MFA would have prevented initial compromise, and payment verification would have stopped the fraudulent transfer.
Conversely, organizations deploying phishing-resistant MFA report dramatic risk reduction. Discord mandated YubiKeys for all employees in 2023, eliminating credential-based account takeover risk entirely. Twitter/X, Cloudflare, and Google implemented similar mandatory security key policies, recognizing that optional deployment was insufficient - users chose convenience over security until mandatory enforcement eliminated the choice. None of these organizations reported successful phishing compromises after deploying security keys, demonstrating that phishing-resistant MFA is effective when properly enforced.
The implementation patterns separating successful defenses from compromises are clear. Organizations that deployed phishing-resistant MFA mandatorily for all users, implemented DMARC reject policies, established dual-channel payment verification procedures, and conducted continuous security awareness training experienced near-zero BEC losses.
Conversely, organizations relying on traditional MFA, lacking email authentication, processing payment changes via email, and providing only annual compliance training lost an average of $129,000 per incident with 73% likelihood of experiencing BEC attacks.
The security investment for the former approach for mid-sized firms costs a fraction of a single BEC incident.
Making these defenses operational in your environment
- Start with payment verification procedures today—no budget required, immediate risk reduction.
- Create a spreadsheet of all vendors, suppliers, and clients you exchange money with, including phone numbers obtained from contracts, invoices, or publicly listed contact information.
- Do not use phone numbers from emails, as these could be attacker-controlled. Distribute this trusted contact list to all finance personnel.
- Institute a policy: any email requesting banking detail changes or unexpected payment instructions requires callback verification using only numbers from this list.
- Document verification calls. Make this procedure non-negotiable—even if the CFO sends the request internally, call to verify. Thread hijacking and compromised executive accounts mean trust but verify applies universally.
- Configure SPF, DKIM, and DMARC. Log into your domain registrar’s DNS management (GoDaddy, Namecheap, Cloudflare, etc.) and add the TXT records. For Office 365 SPF:
v=spf1 include:spf.protection.outlook.com -all.- For DKIM, enable signing in Office 365 admin center, then publish the provided CNAME records.
- For initial DMARC:
v=DMARC1; p=none; rua=mailto:[email protected]; pct=100. - If you’re unfamiliar with DNS management, your IT service provider can implement these records in under an hour.
- Monitor DMARC reports weekly using dmarcly.com’s free tier or similar services.
- After 30 days with no authentication issues, advance to
p=quarantine. After 90 days, advance top=reject. This phased approach prevents blocking legitimate email while progressively hardening defenses. - You can also check out DNSTwist, which resolves misspellings of your domain. Take a close look at sites with mail servers you don’t recognize. Block those domains and understand your customers may be getting emails from those.
- Order FIDO2 security keys immediately for privileged users. For a typical deployment, order from Yubico.com (YubiKey 5 NFC) or Amazon Business.
- Purchase two keys per user—primary and backup.
- Schedule individual enrollment sessions where you walk users through registering keys in Azure AD and testing authentication. Provide written guides with screenshots.
- Document the backup key storage location policy—typically a secure location at the user’s home, not in the same bag as their primary key.
- Configure Azure AD conditional access policies the same week keys arrive.
- Policy 1: “Require phishing-resistant MFA for privileged users,” targeting Global Admins, Security Admins, Exchange Admins, all partners/executives, and all finance team members. Set access controls to require authentication strength “Phishing-resistant MFA,” which includes FIDO2 and certificate-based authentication.
- Policy 2: “Block legacy authentication,” targeting all users, client apps “Exchange ActiveSync” and “Other clients,” access control “Block.”
- Policy 3: “Geographic restrictions,” blocking authentication from countries where your firm doesn’t operate (Russia, China, Nigeria, etc. depending on your risk tolerance). Test policies with your own admin account before enabling for all users.
- Deploy Microsoft Defender for Office 365 or equivalent email security platform. For firms already using Office 365, upgrade licenses from E3 to E3 + Defender P1.
- Configure Safe Links to rewrite URLs and detonate them in sandboxes before delivery.
- Enable Safe Attachments to analyze files in isolated environments. Set anti-phishing policies to aggressive mode.
- Configure impersonation protection by adding executives, partners, and finance personnel to the protected users list.
- Enable mailbox intelligence and spoof intelligence.
- Set actions for high-confidence phishing to “Quarantine” with admin notification. These configurations occur in Microsoft 365 Defender portal under Email & Collaboration > Policies.
- Establish log monitoring even without a full SIEM implementation.
- Configure Azure AD to forward sign-in logs to a Log Analytics workspace (setup takes 30 minutes, costs ~$50-100 per month for typical firm).
- Create workbook queries for the impossible travel detection, SessionId anomalies, and inbox rule creation patterns detailed earlier.
- Set up email alerts when these queries return results.
- Assign a security-focused individual to review alerts daily—this could be an internal IT admin or outsourced SOC service. The goal is detection within hours rather than discovering compromises weeks later when BEC fraud is complete.
- Implement security awareness training with a phishing simulation platform. KnowBe4 offers packages starting at $3-5 per user per month; Proofpoint and others offer similar entry tiers.
- After platform setup, import user email addresses and enable automated training delivery when users click simulations.
- Track phishing click rate (should decline from ~30-40% baseline to under 5% within a year, ideally) and email reporting rate (should increase to over 60% within 12 months). Celebrate improvements publicly—recognize users who consistently report phishing simulations, creating positive reinforcement rather than punishment culture.
- Test your defenses quarterly.
- Send realistic phishing simulations: government bid proposal PDFs with QR codes, supplier cyberattack banking change requests, invoice thread hijacks.
- Test payment verification procedures by having a partner send a fake banking change email to finance and verifying staff call to confirm before processing.
- Conduct tabletop exercises where you discuss scenario: “A partner’s email account is compromised and sends fraudulent wire transfer instructions. Walk through our response procedure.” These exercises identify gaps before real incidents exploit them.
- Obtain a penetration test from a reputable firm that understands your industry and can provide a comprehensive report with strategic recommendations.
- Document everything in a security procedures manual: payment verification procedures, incident reporting process, MFA enrollment instructions, who to contact for security questions, and incident response playbooks.
- Make this accessible to all staff in SharePoint or your document management system.
- Review and update quarterly based on new threats, incidents, or procedural improvements. This documentation ensures security persists beyond institutional knowledge and supports compliance requirements.
The path forward
TA4903 and EvilProxy represent the current state of financially motivated cybercrime targeting professional services: sophisticated, persistent, and specifically designed to bypass traditional MFA and email security. The threat actor’s evolution from simple spoofing to QR code phishing, session hijacking, and thread-based BEC demonstrates continuous adaptation that makes static defenses insufficient. Your security posture must match this operational tempo with phishing-resistant authentication, email authentication enforcement, payment verification procedures, continuous monitoring, and ongoing user training.
The critical success factors are mandatory enforcement of phishing-resistant MFA rather than optional deployment, DMARC reject policy rather than monitoring, callback verification for every payment change without exception, continuous monthly training rather than annual compliance exercises, and active log monitoring for post-compromise detection rather than discovering breaches through fraud investigation.
Organizations implementing half-measures—traditional MFA, DMARC in monitoring mode, optional verification procedures, annual training only—experience compromise rates similar to unprotected firms. Full deployment of layered controls delivers the risk reduction.
Begin today with the zero-cost, high-impact actions: establish payment verification procedures, schedule DNS configuration for email authentication, and brief all staff on TA4903 targeting of accounting firms.
Order FIDO2 security keys this week. Configure conditional access policies within two weeks. Launch continuous security awareness training within 30 days. Test your defenses quarterly through simulations and tabletop exercises. Document everything, measure effectiveness through behavioral metrics, and adjust based on results and evolving threats.
The accounting and professional services industry will remain a primary target for financially motivated threat actors because you handle client funds, process invoices, and manage financial transactions—exactly what TA4903 seeks to exploit. The question isn’t whether attacks will continue but whether your defenses will stop them. Every control detailed in this guide has been proven effective in real-world deployments. The tools exist, the implementation path is clear, and the cost is substantially less than a single BEC incident. Not to mention you’ll satisfy the IRS Cybersecurity guidelines in their publication 4557. Your firm’s financial security and client trust depend on implementing these defenses now.





