Welcome to the second installment of our Strategic CISO Series—a collection of guides focused on turning operational security work into strategic wins. Read Part 0 Before the Test — When Your Startup is Really Ready for Penetration Testing.
In this article
- Why Timing Matters
- Four Strategic Windows for Penetration Testing
- Window 1: The Executive Showcase (6-8 Weeks Before Major Presentations)
- Window 2: The Industry Response (Post-Competitor Breach or Major CVE)
- Window 3: Preemptive Strike Before Compliance (Before Audits, Not During)
- Window 4: The Product Security Story (Pre-Launch or Major Release)
- The Long Game: Year-Over-Year Comparison
- Strategic Planning: Your Decision Framework
- Strategic Timing: Common Pitfalls to Avoid
- What to Look for in a Vendor (If You Want Strategic Timing to Work)
- The Bottom Line
- Discuss Your Strategic Testing Timeline
While most security leaders schedule assessments around audit deadlines, the timing of your security testing creates opportunities to demonstrate proactive leadership, present measurable improvements, and position security as a business enabler rather than a cost center.
Your executive leadership review is eight weeks away, scheduled for 15 minutes between the CFO’s budget presentation and lunch. You know you need to talk about security, but leading with “we’re compliant” sounds like you’re just checking boxes, and you definitely can’t lead with “here are all our vulnerabilities.”
This is a tightrope every security leader walks. You need to discuss security in a way that demonstrates both vigilance and value, without creating panic or appearing reactive.
The timing of your penetration test is just as strategic as the test itself.
A well-timed pen test validates your security posture, creates a narrative of proactive leadership, provides concrete metrics to present, and positions you as strategic rather than operational.
A poorly timed test leaves you scrambling to explain findings without a remediation story, or, worse, presenting stale data that makes the board question what you’re doing with your time.
Why Timing Matters
Every penetration test delivers technical findings. Strategic penetration tests deliver business outcomes.
The difference isn’t in the testing methodology or even expertise - it’s in when you test and what you do with the results. Testing six weeks before a board meeting gives you time to remediate findings and walk into that meeting with a complete narrative of proactive security leadership. Testing two weeks before forces you to either hide findings or present problems without solutions.
Strategic timing enables you to:
- Control the narrative: You found the vulnerabilities, you fixed them, you validated the remediation
- Demonstrate maturity: Proactive risk management rather than reactive crisis response
- Measure improvement: Year-over-year comparisons that prove your security investments are working
- Align with business moments: Product launches, board meetings, compliance audits, customer onboarding
- Justify spending and resources: You know significant work needs to be done as verified by a third party; this can bolster support for increased headcount or tool budget
Security leaders who master timing use their penetration tests to manufacture strategic wins. Those who don’t find themselves constantly explaining why they’re behind.
Try our Strategic Testing Timeline Planner → adversis.github.io/testing-timeline
Four Strategic Windows for Penetration Testing
Window 1: The Executive Showcase (6-8 Weeks Before Major Presentations)

Strategic play: Commission a penetration test that completes 6-8 weeks before your key stakeholder presentation—whether that’s your board, executive leadership team, quarterly business review, or audit committee—giving you time to remediate critical findings and present a complete narrative of proactive security management.
What you can say to stakeholders:
“We proactively commissioned an independent security assessment to validate our security posture”
“We identified and remediated X vulnerabilities before they could be exploited”
“Our security controls are performing as designed, with only minor findings that have been addressed”
Why the timing works: You’re controlling the narrative. You found the problems. You fixed the problems. You’re demonstrating maturity and proactive risk management. The leadership team sees leadership, not firefighting.
Timeline breakdown:
- Week -1: Engagement ready with access and information
- Week 0: Engagement starts
- Week 1-2: Testing occurs
- Week 3: Report delivered
- Week 3-5: Your team remediates critical and high findings
- Week 6: Retest validates fixes (more on this later)
- Week 7-8: You prepare stakeholder materials with clean data
Critical consideration: This only works if your vendor can deliver a report quickly and your team has the bandwidth to remediate. If the report sits for three weeks before anyone looks at it, you’re losing your window.
When evaluating vendors, ask: “What’s your turnaround time from test completion to report delivery?” Anything over 5-7 business days will compress your remediation timeline.
What you need from your vendor to make this work
- Fast report turnaround (days, not weeks)
- Clear prioritization in the report so you know what to fix first
- Separation of “quick wins” from “architectural changes required” - some fixes take 2 days, others will take 2 quarters
- A comprehensive deep dive with your team to discuss remediation steps to get a head start on those efforts.
- Included retest hours so you can validate fixes and present clean results
Executive slide
Security Assessment Results - Q4 2024

All critical and high-severity findings identified in our independent security assessment have been remediated and retested. This validates that our security investments are working as designed.
This demonstrates proactive risk management. This is strategic security leadership.
Window 2: The Industry Response (Post-Competitor Breach or Major CVE)

The strategic play: When a major breach hits your industry or a critical vulnerability affects your tech stack, commission a targeted assessment.
Business context: Your leadership team just read about a competitor getting breached, or a major CVE dropped that affects the technology you use. They’re wondering: “Are we vulnerable to this?” Strategic security leaders answer that question before it’s asked.
Triaging whether these things affect your business is a larger conversation. A key consideration for urgency is whether the vulnerability is currently being exploited with publicly released tools, whether you understand your control maturity and attack surface, and the impacts of a compromised affected system. Undergoing security analyses, control audits, purple team partnerships, penetration tests, or red team engagements can help illuminate this uncertainty.
What you can present to the executives:
- “Following the industry incident/named CVE, we immediately commissioned a targeted security assessment to validate our exposure”
- “We moved up our annual penetration test scheduled date and added a targeted scope to validate our controls/patches”
- “We were able to confirm that our security controls prevented this attack vector from being exploitable in our environment”
- “We identified two areas for hardening and implemented fixes within 72 hours”
Why this timing works: Speed and specificity. You’re not waiting for the leadership team to ask the question—you’re answering it before they think of it. This is the difference between reactive and responsive. Reactive is “oh yeah, we should probably check on that.” Responsive is “I’ve already validated our posture and here’s what we found.”
Real-world example: When Log4Shell dropped in December 2021, the CISOs who immediately commissioned targeted pen tests focused on Log4j exploitation were able to report with confidence: “We identified 3 instances, patched them within 48 hours, and validated through penetration testing that we’re no longer vulnerable. No publicly accessible services are vulnerable”
Security leaders who didn’t test were left saying “we think we patched everything”—which is not what leadership wants to hear in crisis moments.
What you need from your vendor to make this work:
Industry response timing requires a partner who can mobilize quickly (again, days, not weeks), brings specialized expertise in emergent threats, and provides real-time communication during testing. If they find something critical, you need to know immediately.
Slide that demonstrates responsive leadership
Timeline of Response to Named Breach
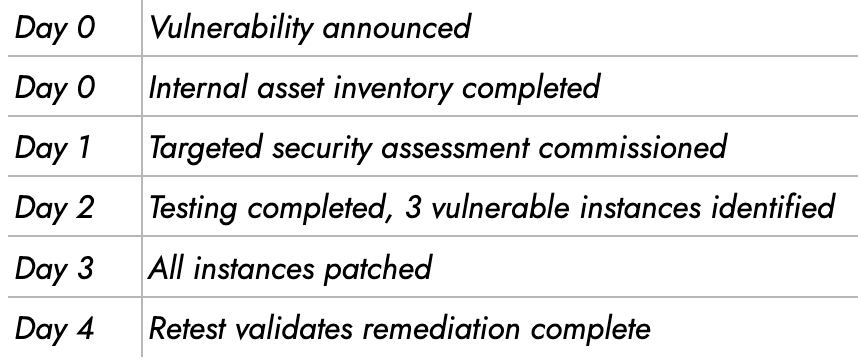
Mean time to remediation: 96 hours from disclosure to validated fix
Demonstrate security operations excellence aligned with business velocity.
Window 3: Preemptive Strike Before Compliance (Before Audits, Not During)

The play: Schedule your pen test 90-120 days before your compliance audit (SOC 2, ISO 27001, PCI, HIPAA, etc.), giving you time to remediate findings before auditors arrive.
The strategic advantage: Many companies schedule penetration tests to coincide with audit requirements, meaning the auditor sees findings around the same time you do. Strategic security leaders validate controls before audits, transforming potential stressors into demonstrations of security maturity.
What you can say to your stakeholders (and auditors):
- “We completed our annual penetration test in Q2, remediated all findings, and are now prepared for our Q3 audit”
- “Our audit prep includes pre-validated security controls, reducing audit friction and timeline”
- “We identified and resolved security gaps before the auditor found them, demonstrating mature security practices”
Why this timing works: Auditors love controls that are already validated. If your pen test is complete, findings are remediated, and you walk into the audit with clean documentation, you’ve just turned a potential stressor into a demonstration of maturity. Plus, if the pen test does find something gnarly, you have time to fix it before the auditor asks about it.
The awkward scenario this avoids: Your SOC 2 audit is scheduled for October. You commission your pen test in September “to have fresh results for the audit.” The pen test finds a critical SQL injection vulnerability. Now you’re in remediation mode during the audit, explaining to both the auditor and your board why this exists. Even if you fix it quickly, it’s going in the audit report as “finding identified during audit period.”
Compare that to strategic timing: Penetration test in July. Finding discovered and remediated in August. Retested clean in September. Auditor arrives in October and you present a complete package: “Here’s our penetration test from Q3, here’s the remediation, here’s the retest validation.” Clean audit. Confident leadership team.
Ask your vendor to include retesting so you can show “finding closed” before the audit.
The slide that demonstrates readiness
Compliance Readiness - Audit Prep

“We’ve de-risked the audit process by validating our controls in advance.”
Strategic planning, not last-minute scrambling.
Window 4: The Product Security Story (Pre-Launch or Major Release)

The strategic play: Test new products, major features, or infrastructure changes before they go live and before they attract attacker attention.
Business context: You’re launching a new product, exposing a new API, or making significant architectural changes. Your engineering team is focused on features and performance. Strategic security leaders integrate testing into the launch process rather than treating security as a launch-day concern.
What you can say to the leadership team:
- “We integrated security testing into our launch process, validating our new platform before public release”
- “Security was built into the product roadmap, not bolted on after launch”
- “We identified and resolved 5 security issues in staging, preventing post-launch vulnerabilities”
Why this works: “Shift left” is the mantra, but most companies still treat security as a launch-day or post-launch concern. If you can demonstrate that security testing happened before launch, you’re showing mature DevSecOps practices.
The strategic value: This also creates internal credibility with your engineering team. If you find issues pre-launch and help them fix it before customers are affected, you’re a partner. If you’re constantly pointing out problems in production, you’re a blocker. The perception shapes your ability to influence future projects.
What you need from your vendor to make this work:
- Flexibility to test staging/pre-production environments (not all pen test firms do this well)
- Fast turnaround—product launches don’t wait for 30-day testing cycles
- Developer-friendly reporting—engineers need to understand how to fix issues, not just that issues exist
- Willingness to collaborate with your dev team during testing (some findings need clarification; having a tester available to explain helps remediation)
Winning slide
Product Launch Security Timeline

Security was integrated into the product development cycle, a significant cost savings over findings identified in production
The Long Game: Year-Over-Year Comparison

Strategic security leaders track penetration test results year-over-year and present trends that prove security program effectiveness.
If you’re testing annually (and you should be), the compelling story isn’t “we had fewer findings this year.” It’s “here’s how our security posture has measurably improved.”
Slide demonstrating strategic security leadership
Security Posture Trend (3-Year)
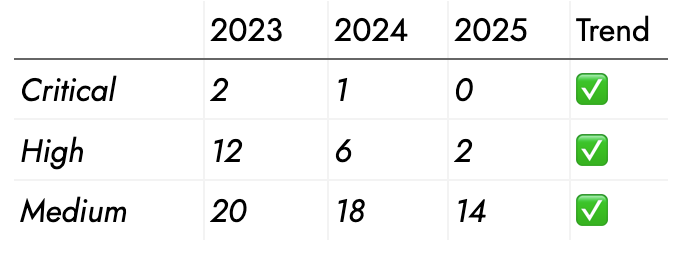
“Over three years, we’ve reduced high-severity findings by 83% and improved our remediation speed by 73%. Our security investments are measurably improving our risk posture.”
That is strategic. That’s budget justification. This proves your security program delivers measurable business value.
What you need from your vendor to make this work:
- Consistency in testing methodology year-over-year (if you change vendors or scope dramatically, comparisons become meaningless)
- Historical data maintained—compare prior data
- Industry benchmarking—if your vendor tests other companies in your industry/size, anonymized comparison data is valuable
Strategic Planning: Your Decision Framework
Choose the timing window that best serves your strategic goals:
Choose Window 1 (Pre-Executive Showcase) if:
- You have a major stakeholder meeting or strategic planning session coming up
- You want to demonstrate proactive security leadership with validated results
- You have bandwidth for remediation between test and presentation
Choose Window 2 (Industry Response) if:
- A major breach just hit your industry or a competitor
- A critical CVE affects your tech stack
- Your leadership team is asking “are we vulnerable to X?”
Choose Window 3 (Compliance Preemptive Strike) if:
- You have an upcoming audit (SOC 2, ISO, PCI, HIPAA, etc.)
- You want to de-risk the audit process with pre-validated controls
- You need compliance documentation for customers/partners
Choose Window 4 (Product Security Story) if:
- You’re launching a new product or major feature
- You’re making significant infrastructure changes
- You want to integrate security into the development lifecycle
Most strategic approach: Combine windows 3 and 4 on a predictable cadence, and use windows 1 and 2 opportunistically.
Example annual calendar:
- Q1: Post-product launch pen test (Window 4)
- Q2: Pre-compliance audit pen test (Window 3)
- Q3: Prep Q2 results for executive meeting (Window 1)
- Q4: Respond to any industry incidents as needed (Window 2)
This gives you a drumbeat of security validation, predictable testing cadence, and strategic moments to showcase your program’s effectiveness.
Strategic Timing: Common Pitfalls to Avoid

Understanding common timing mistakes helps you plan more effectively:
Insufficient remediation window: You commission a pen test two weeks before your executive meeting. When the report comes back with critical findings, you have no time to remediate. You walk into the leadership meeting and either:
- Hide the findings (maybe a resume generating event)
- Present the findings with no remediation story (looks reactive and unprepared)
- Cancel your security update (looks like you’re avoiding the topic)
Testing during product launches: You test right before a major product launch. Pen test finds a critical issue. Now you’re choosing between:
- Delay the launch (business impact, everyone blames security)
- Launch anyway and fix it later (risk acceptance you didn’t plan for, hope it’s not exploited)
- Rush a fix without proper testing (potentially introducing new issues)
Testing during audits: You test during your audit. Findings emerge mid-audit. Auditor documents them as “control failures identified during assessment.” Even if you fix them immediately, they’re in the audit report, creating customer concerns and remediation requirements.
Inconsistent testing methodologies: Changing the testing scope drastically or switching vendors every six months makes trend analysis difficult, since you can’t demonstrate improvement when the methodology changes. Strategic planning maintains consistent testing approaches that enable year-over-year comparison.
All of these are avoidable with better timing.
What to Look for in a Vendor (If You Want Strategic Timing to Work)
Strategic timing only works when your security testing partner understands both technical depth and business context. Key capabilities that enable strategic timing:
1. Fast report turnaround: Reports delivered within 5-7 business days, so you control your timeline and have adequate remediation windows. Ask: “From test completion to report delivery, what’s your timeline?”
2. Built-in retesting: Validate remediation before presentations. Retest hours should be included in every engagement, not sold separately or requiring additional procurement cycles.
3. Collaborative approach: Testing partners who work alongside your team during remediation, not vendors who deliver reports and disappear. Some findings need clarification; having testers available accelerates remediation.
4. Real-time critical escalation: If they find something severe, you should know during testing, not in a report weeks later. Ask: “If you find a critical vulnerability, what’s your escalation process?”
5. Flexible scheduling: Strategic windows sometimes have tight timelines. Can they start in 2 weeks? Or is their lead time 8+ weeks?
6. Executive reporting capability: Technical reports are necessary; executive summaries are strategic. If appropriate for the assessment, make sure they provide executive-ready documentation, not just technical findings.
The Bottom Line
Strategic timing transforms security testing from an operational necessity into a controlled narrative.
A penetration test itself takes 80 hours. The strategic value comes from when you test and what you do with the results.
A little planning around timing makes your penetration test 10x more valuable to your career and your company. Testing aligned with executive meetings demonstrates proactive leadership. Testing before audits de-risks compliance. Testing before product launches integrates security into development. Testing after major CVEs demonstrates responsive operations.
The technical findings do matter. But the business outcomes matter more.
Security leaders who master timing use their penetration tests to prove program effectiveness, justify security investments, and position security as a business enabler. Those who treat testing as a compliance checkbox miss the strategic opportunity.
Your next steps
- Map your executive leadership meetings, compliance audits, and product launches
- Identify which strategic window best serves your goals.
- Plan your testing calendar around business moments that matter.
Strategic timing turns security testing into strategic advantage.
Discuss Your Strategic Testing Timeline
Schedule a consultation to discuss aligning your security assessments with stakeholder presentations, compliance deadlines, and product launches. Our team brings specialized offensive security expertise from Fortune 500 environments—we understand both the technical testing and the strategic timing that makes results valuable to your business.
Learn More About Our Approach
Want to see how your current pen test schedule aligns with your strategic calendar? We created a simple timeline calculator that maps your stakeholder meetings, audits, and product launches to optimal testing windows. It takes 5 minutes and shows you whether you’re leaving strategic opportunities on the table.
Try our Strategic Testing Timeline Planner → adversis.github.io/testing-timeline
Adversis stands in your corner, providing specialized offensive security testing, strategic compliance advisory, and expert project consulting to technical leaders at high-tech companies. Security expertise that accelerates your business.





